Do you want to buy limited-edition sneakers, want to scrape data from the Internet, or want to check your keywords ranking on Google without getting blocked?
Then you need private proxies. Without them, you are limited to a few numbers of requests you can make to web servers per minute. If you cross the line, your IP address gets blocked or you are asked to solve captchas.
In this article, I will be discussing private proxies. You’ll learn about what private proxies are, reasons for using them and their types of authentication.

What is a Private Proxy?
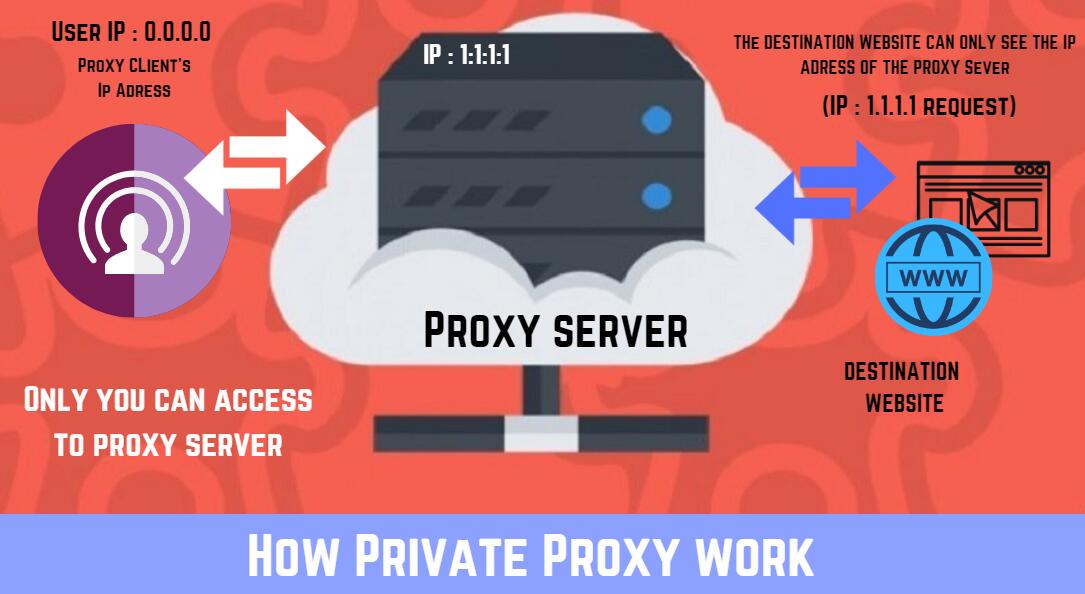
Private proxy is a dedicated IP address assigned only to one person to provide him/her with anonymity in other to prevent censorship, surveillance, and circumvent geolocation restrictions online.
Otherwise known as a dedicated IP address, a private proxy masks the real IP address of a user and presents the dedicated IP address as the user’s IP address. This helps the user remain anonymous.
Unlike in public and shared proxies, private proxy owners enjoy a high level of privacy and have full control rights over their private proxies.
They do not have to be wary of their neighbors’ activities. Neighbors, in this case, are other users of the IP address. When you’re using a shared IP address, the activity of one user of the IP address on a website might get all of you restricted from accessing the offending website. However, since private proxies are dedicated to one user at a time, they are expensive compared to their counterparts.
Why use Private Proxies?
What are private proxies good for? There are lots of reason to use the proxies, Here we mainly discuss why people buy the paid private proxies for their demand,
-
Sneaker Coping Using Sneaker Proxies
Have you walked past a mall before and you see people lined up waiting for hours just to get a pair of newly released sneakers that are high in demand?
People love sneakers because of their comfortable feel on the feet and the aesthetic they add to your general appearance. While people spend countless hours waiting at the mall under the scorching sun, some set of people remain in their rooms and still end up buying faster and even more pairs – thanks to sneaker bots.
A sneaker bot is automation software that aids in buying high demand shoes really really fast. Some go as far as buying many of those shoes. Without sneaker bots, you cannot.
Nike and Adidas are at the forefront of selling high-in-demand quality sneakers. Interestingly, they have designed their systems in such a way that requests through sneaker bots are blocked.
- Guide to Copping Sneakers Online with proxies, bots and server
- How People Use Proxies to Buy Nike and Supreme Shoes
This is because they cheat the system and buy more than just a pair which the owners of the bot will end up selling to make a profit. However, with the help of sneaker proxies, sneaker coping has been made possible using sneaker bots. Nike has been fighting the use of sneaker bots for a while and they have been successful in the past.
However, developers are increasingly finding ways to make their bots work. They need private proxies made specifically for sneaker bots which they can use to mimic different users at different locations in other to buy those sneakers. Limited edition sneakers sell within a day or even a few hours. With sneaker bots, one can buy more than one and make profits selling them.
-
Spoof GPS Location for Gaming Purposes Using Gaming Proxies
Pokémon Go is one of the most popular games that have surfaced since the coming of smartphones. Many people old and young are seen catching Pokémon even while walking on the streets. While the game is addictive and rewarding to play, Pokémon is not available in many countries.
Your country might be the reason you’re not catching a lot of Pokémon. In some countries, the game has been outrightly banned. You cannot play Pokémon in Iran. It is not just allowed. In many Asian countries, lovers of the game are still waiting for their countries to be added to the list of countries with Pokémon.
However, while they wait and people in Iran are locked out, some users have devised a means of spoofing their GPS location so they could catch Pokémon in other countries. These gamers make use of gaming proxies to hide their location and play the game as if they are in another country. Private proxies are used in most cases.
- Read more: 5 Ways to Use Proxies for Pokemon Go Hacking
It is possible to use shared proxies but your security is not guaranteed as hackers that steal your Pokémon and inject a virus into your system. If you use private proxies, you’re more secured since you aren’t using the proxy with anyone. Going for private proxies will cost you money but your security is assured.
-
Social Automation Using Social Proxies
Instagram, Snapchat, Twitter, and Pinterest are money makers for Internet marketers. While most users of these social networks are there purely for having fun, keeping up with friends and whiling away time, some people are making huge money on these social network platforms.
You’ll see someone having over 10 business accounts on Instagram, the same person has such number or even more on Twitter, Facebook, and Pinterest.
How do you think such a person could possibly run this number of accounts without automating their activities? Have you had any experience of accounts following you if you follow them or liked their post and the follow back was fast? That’s the work of a bot.
Social media bots have been made to operate different accounts and mimic different locations in other to avoid been blocked. This is because social media sites hate these automation tools since they do not add to their profit but the cost of running their servers.
However, by using social proxies that are bought from private proxy service, they escape been detected. This is a low cost of avoiding a ban. You can also set up your own proxy server just like it will require a lot of expertise.
-
SEO Auditing with SEO proxies
Search engines such as Google, Bing, and Yandex can make you a lot of money if you rank on them. A lot of businesses generate leads and even sales from the traffic coming from these popular search engines. Because traffic is not paid for, it is the best choice among Internet marketers.
However, ranking on the first pages of these search engines is not an easy task. Take Google, for instance, it has over 200 ranking factors which it uses to rank pages on its result pages. While earning a good ranking has to do with the quality of your content and your backlink profile, maintaining it and moving up the ranking isn’t an easy thing.
You need to do a lot of SEO auditing like checking your keyword ranking. This is done with the use of automated rank checkers. They can not only check your ranking based on your current location, but they can check how your pages are ranking in other locations as well.
This is because they use SEO proxies that can check your location and mimic different human behaviors. If you use software that provide rank monitoring as a service, you won’t need to pay for private proxies to get this done since the developers of the software like SEMrush (Get 30 Day free trial Here!) had already done that on your behave. However, if you use software like ScrapeBox or custom software, you need private proxies to get them to work.
-
Web Scraping and Crawling
E-commerce stores like Amazon and Aliexpress are product sales data of heaven. They are packed with lots of information about products, their sellers and how people perceive them. Businesses are interested in those data so they can use them to make decisions.
Sometimes in the past, I had helped someone scrape over 500K reviews of shoes and clothes. There’s no way Amazon will allow me to do that without a proxy. Why? Read this post to know E-commerce proxies when scraping E-commerce stores? I tried at first and after a few scrapes, I was denied access and I had to use private proxies to continue.
Not only e-commerce stores, Apps stores like Google Play Store and Apple’s App Store is also a huge library of information for developers. After putting an application on the store and people download them, they leave reviews on their perceived value.
These developers usually need to get these customers reviews on their apps to know if there are bugs to be fixed or parts of the user experience they need to adjust to better serve their customers. Because of the number of requests they would want to send, they usually make use of private proxies to evade being noticed and blocked.
-
Getting More Exposure Using Craigslist Proxies
Craigslist is a classified ads site for selling products. This website gets over 500 million visitors monthly of which over 95 percent of them are from the US. Normally, you do not need the proxy to post ads on Craigslist.
However, if you need to create more awareness for your product by posting different ads with different IP addresses, you have to use a proxy. And not just any proxy but Craigslist proxies. By using Craigslist proxies, sellers on Craigslist are able to get more people to view their products and by so doing, get more opportunities to sell their products.
Related: The Ultimate Guide to Scraping Craigslist Data with Software.
-
Buy Tickets with Ticketmaster Proxies
Some tickets get sold out in hours. People are on their computer waiting to hear news about them being on sales. Upon hearing such news, they rush to buy them. Unfortunately, many of those tickets are location-dependent, making things more difficult for those living in other locations. However, with Ticketmaster proxies, you can bypass those restrictions.
Live in the US and buy tickets in the UK using Ticketmaster proxies. Ticketmaster is a ticket sales and distribution company based in the United States. This company places restrictions on tickets one can buy based on their location. With Ticketmaster proxies, one can bypass this restriction and buy tickets for theatre, concerts, sport, family events, clubs and more.
How to use a private proxy?
Proxies, in general, are not made for any specific platform. They can be used in Windows, Mac, Android, iOS, Linux, and even embedded systems, for proxies can be used on every browser, no need to download any softwares.
Comparing to other public proxies or free proxies, You need to Authenticate the proxy when you're using the private proxy.
They are application-centric. You can enter them into the settings of the application you want to use to access the Internet. Most popular browsers have a proxy setting area where you can enter the proxy.
ScrapeBox and other tools also have a provision for that. However, regardless of the software, you plan using the proxy for, you need to prove you’re the rightful owner by authentication.
There are two methods of authenticating a private proxy. These are by using regular username and password or IP authentication.
-
Username and Password Authentication
Using a username and password for authentication is the most popular form of authentication. Internet users are already used to it, and as such, there’s nothing new in this case.
When you purchase a proxy, they will be accompanied by a username and password. You can always change the password. In fact, it is advisable to always change the password after a while.
-
IP Authentication
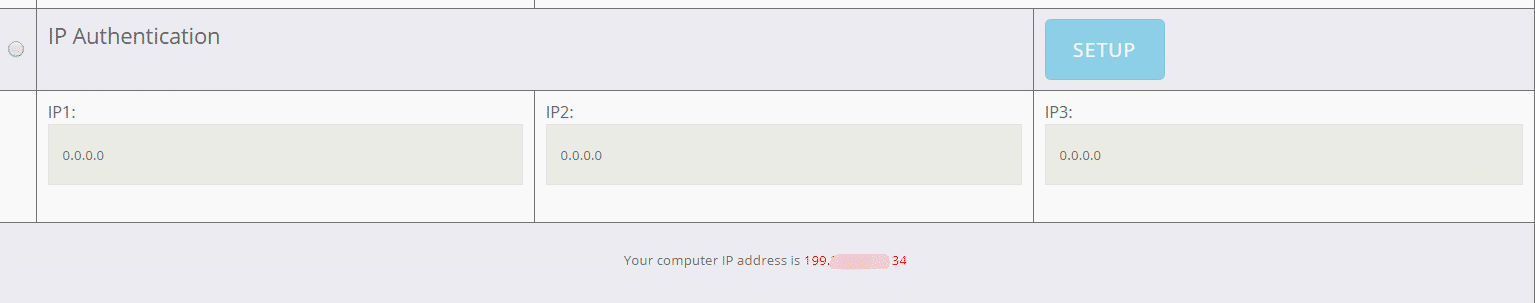
Otherwise known as IP whitelisting, IP authentication is simply the type of authentication where you enter your real IP (provided by your ISP) in the list of the whitelisted IP addresses in the private proxy you bought. This type of authentication ensures that only IP addresses whitelisted can actually use the proxy.
Read more: Username and Password or IP Authentication: Which is Better?
Conclusion
Indeed, dedicated IP addresses otherwise known as private proxies are some of the options used by online users to hide their true IP addresses by using an intermediate server.
They are useful for web scraping, social media automation, and bypassing geolocation restrictions among others. When next you need to mask your IP address online, try using a private proxy and your identity will be hidden as you wish.