The wonderful world of proxies is centered around one key concept: anonymity. People get proxies to be anonymous online. It’s a bit like wearing the Guy Fawkes mask every time you boot up your computer. Whether you’re an average joe who is slightly wary of an overzealous National Security
Agency, entertainment-should-be-free capitalism eschewing individual that loves to torrent every last piece of media out there, or a full-on black hat technician who sets up TOR, proxies are there for you.
More than ever before, actually. Proxies and VPNs (a service like proxies but with a tweak) are on the rise. This is due to the lack of clarity that governs the inner workings of the web, and how easy it is to get your identity stolen.
It can be as simple as not wanting hackers to find your IP address, and therefore tap into your computer. The solution for that and everything beyond? Get and use a proxy.
The Proxy Irony
Within the seeming web of safety that proxies allow lie a couple not so well known ironies that, from my perspective, are pretty hilarious.
The first is that a lot of proxies aren’t actually anonymous.
Shocked? Don’t be.
Most proxies are free, and free proxies are far from anonymous or safe. Yes, if you can get a free proxy to work in your favor it will hide your IP address for certain activities, and specifically from sites like Google.
However, if you boot up a free proxy into your browser, visit websites, and at some point enter any password and username combination, you’re open to risk.
While your destination website might not see your IP address, the person or company who owns that free public proxy can, and has intimate access to your computer, what your browser displays, and a host of other information.
One way to combat this is to always use private proxies. These come at a price, but that price is often small, and will provide a more thorough peace of mind when it comes to anonymity and security than free proxies.
Below I’ll get into two methods of increasing security for private proxies — username and password combinations, or IP authentication — and which is better.
First, though, know that the second proxy irony is that even private proxies are subject to crises of true anonymity.
If a hacker or government agency is dedicated enough it can retrieve the information you’ve accessed even when you’re on a proxy, and even if that proxy is private. This is because proxies by nature are not as secure as VPN, whose technology creates an impenetrable tunnel between users so that you actually cannot access the information.
Unless you’re a serious hacker yourself, you probably don’t need to worry about this. And if you are a serious hacker, you should already know this.
If we can assume that you don’t fall into that category, a private proxy should be more than enough to keep you actually anonymous.
That said, you’ll need to be sure the proxy provider gives you at least one option for secure authentication.
Types of Private Proxy Authentication
One of the keys to making sure your private proxies are legitimately anonymous is if they come with authentication.
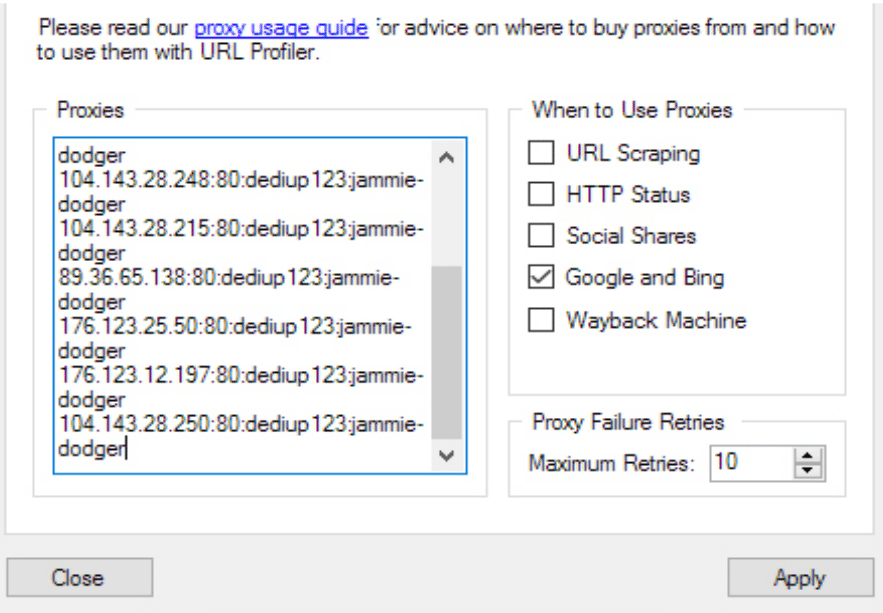
This should be stated very clearly on your proxy provider’s website. If it’s not, send an email to ask what kind of authentication they use. Both types — username and password, or IP — are valid, but they have their pros and cons.
Username and Password Authentication
This is the more common of the two main types, and the one you’ll be most familiar with.
Similar to creating a bank account, joining an email marketing service, or creating any new social media account, username and password authentication is the standard by which we protect ourselves in today’s society.
In the case of proxies that is equally true. When you buy a single (or more likely, a bulk batch) of private proxies, you want to make sure they are used only by you. After all, a private proxy is still just a proxy, which is basically an open port that anyone can connect to.
What makes your proxies safe is that to connect to that port, you have to have the username and password, thereby authenticating your access.
Typically, upon purchase, your provider will send you an email with a list of IP addresses, a username, and a password. In most cases, it will look like this:
111.222.3.444:80:55555name:xyz123
For those not embroiled in the proxy world, that can come out a bit confusing. Of course I’ve used a number and numeral combination that is very fake, but it should correspond roughly to what your provider has given you.
Below I’ll break each section down. Note that colons separate each section (not periods), so you can always go by where the colon is in a line like the one above.
- 111.222.3.444 – This is the IP address of your proxy. When anything asks for a specific IP address, use this number.
- 80 – This is the port number. 80 is a common port number. Other common port numbers are 8080, 3127 and 3128.
- 55555name – This is your username, and can really be anything. I based this particular structure off my most recent batch of proxies, which were given to me with a username and password combination. Often your provider will put numbers in here that correspond to your user number, and the name you registered the proxies with.
- xyz123 – This is your password.
The IP numbers will be different for every proxy you buy, but the ports, username, and passwords are often the same. This is typically to simplify the signing up process.
Your provider should allow you to change your password. This is a pretty important aspect, as you may want to have different passwords for different IP addresses, and you may need to change passwords frequently.
You won’t likely be able to change your username, but your IPs and ports can usually be switched out upon request, depending on what you’re using your proxies for.
How to Log in With Username and Password
Just like the banks and social media accounts I mentioned earlier, logging in with this information is really easy. It’s done in two ways.
Proxy Provider Web Interface
The first way to access and alter any of these settings is to actually log into your proxy provider account. This may be the same username and password as your proxies, but it may be different. Make sure you check to see which is which, but if they’re the same it will be simple.
Most proxy providers have a web-based user interface you can log into, and in that interface, you can see all the proxies you’ve paid for, what their status is, what your subscription plan is like, etc.
This is where you should be able to change your password and make any special requests. In some cases, you can assign specific functions to your proxies in this panel, but most often it’s just a portal for you to see what you have registered with your provider.
Specific Proxy Settings
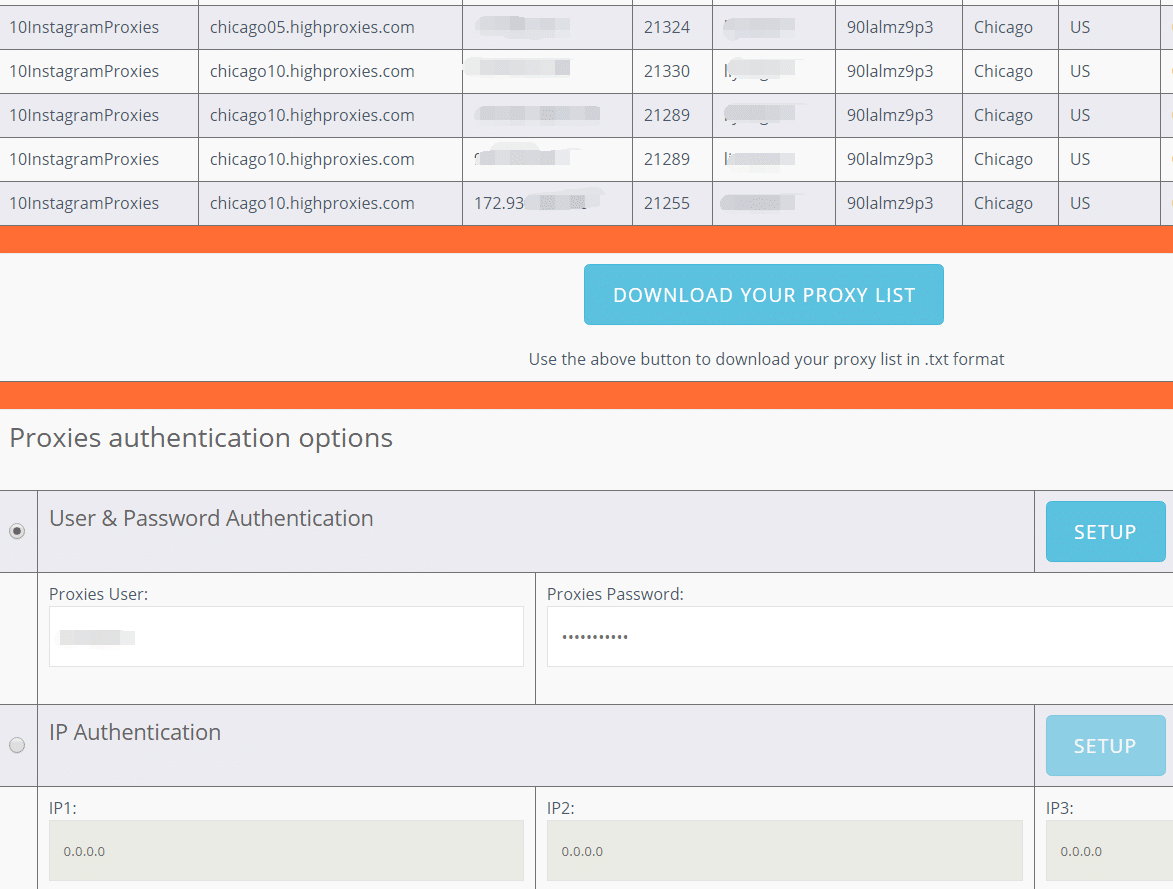
There are many types of specific proxy settings. You can access them in your computer system preferences, in web browsers, in third-party software applications. Almost anything that you plan to use a proxy for will have a space for you to enter that proxy.
In every case you’ll be asked for all of the above information — an IP address, a port number, a username, and a password. Fill in each of these correctly, and your computer or browser will start using that proxy to connect to the web.
Anonymity at its finest.
IP Authentication
This version of proxy authentication is less common and quite different.
To use proxies in your home you’ll need to have internet access, and when you get internet you will be assigned an IP address by your Internet Service Provider (ISP). This is the IP address you’re trying to hide.
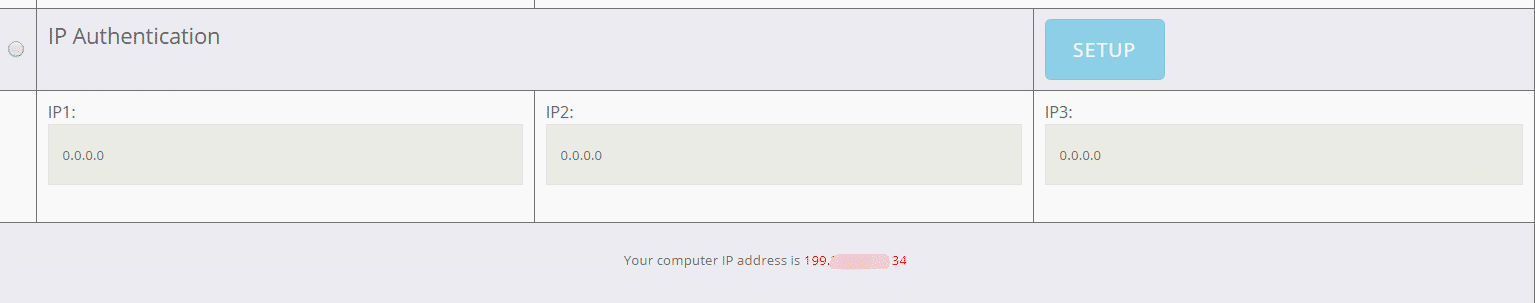
Proxy providers that don’t use username and password authentication (for reasons I’ll get into below) will actually use your ISP IP address to authenticate your proxies.
This means that instead of an email that contains a password that you can change, and a username, you will be automatically verified to use your proxies by your IP address.
You can usually whitelist 1-15 IP addresses with your provider, which means any time you try to use your proxies with any of those IP addresses, it will work automatically.
This process seems simple, and it can be, but it also has a number of pros and cons, which I’ll get into below.
Which Is Better?
This is the big question you’ve been waiting and reading for. As in all things, there is no clear cut answer. Sorry to disappoint.
Each method of authentication has its merits and downfalls, so if you’re trying to make a decision, read below to see which scenario is best for you.
The Pros and Cons of Username and Password Proxy Authentication
I laid out the way username and password authentication works so specifically above because it is imperative to understand the pros and cons of the system.
The best part of this system is the familiarity. We’re used to having passwords and usernames, as its the most common system around. This will make those who are new to proxies adapt more quickly.
The con of that follows quickly behind — it can be another batch of information to remember, write down, and use. Some people don’t want another password they have to keep track of. What type of person are you?
Another pro is that you’ll have more control and flexibility over your proxy access. You can change the password easily — for those who are worried about their passwords getting hacked, this is a way to fend off such attacks.
The con of this is that you have to potentially change your password often. In some ways, IP authentication is more secure because your proxies aren’t subject to a password being cracked.
The final major pro is that you can access your proxies from anywhere. As you’ll see below, the IP authentication method limits you (potentially), while the username and password authentication method make it so you can log into your proxies, and use them, from any location.
The Pros and Cons of IP Authentication
Since IP authentication is the more unique of the two methods, you’ll find it has more varied pros and cons.
The major pro is that you’ll never have to log in any information for your proxies. This can save you a lot of time if you have, say, a batch of 20 proxies and would normally have to enter different passwords for them. IP authentication takes all of this away — your proxies are automatically authenticated when your provider sees you’re using the designated IP.
Right on its heels, the major con of IP authentication is that it can be very limiting if you travel a lot, or access the internet from different places. Even if you have the full 15 IP addresses whitelisted, working from a coffee shop becomes hard to do with your proxies, because you likely haven’t whitelisted that IP.
One way to combat this is to use a VPN or VPS service. VPNs are a lot like proxies, but different in a number of key ways. However, you can use a VPN to always have the same IP address no matter where you are — you simply log into your VPN, and your IP address will be the one they assign you.
If you whitelist this IP, and always have your VPN on, not only can you use IP authentication proxies from any location but you’ll have a double layer of protection due to your VPN. This is a great system for those who want true anonymity.
The last con to the IP authentication method has to do with dynamic IPs. Some ISPs will give you a static IP address — one that never changes. This will work well for IP authentication because your ISP IP address (typically in your home or office) is always the same.
However, a dynamic IP address is one that changes frequently, without warning. ISPs do this to increase your security, because a constantly changing IP address is much harder to hack. It also means that you’ll have to constantly authorize new IP addresses for your proxy provider.
This is highly situational, so find out if you have a static or dynamic IP address from your ISP.
- Static IP proxy Vs. Rotating IP proxy
- What’s The Difference Between a Proxy and a VPN?
- Residential IP Proxy Vs. Datacenter IP Proxy
Do Your Research, Then Get the Best Deal
Now that the two types of proxy authentication are demystified, you have some research to do. What kind of IP does your ISP provide and what system sounds right for you? After those two questions are answered it’s time to start shopping providers.
For the most part, there won’t be a cost difference in these methods — but some providers don’t have IP authentication, while others only have that option. Go with the best deal you can find from a reputable proxy provider and you’ll be ready to use proxies in no time.






