What do you know about proxies? If you know little, then come in now to learn what proxies are, how they work, their types based on different criteria, and what differentiates them with VPN. Take this to be an introductory article to proxies.

Internet censorship is real – even without them, the problem of accessing local content, restricted content and circumventing national restriction regarding what you can access on the Internet and what you cannot make the use of proxies or other ways of hiding your real IP Address a must. The focus on this article is proxy and that is what we will dwell on. Let take a look at what is a proxy server.
What is a Proxy Server?
A proxy server is an intermediate server between a computer and the Internet. It serves as a gateway between a client computer and websites. When making use of proxies, requests you send to websites pass through them before getting to the website, and as such, depending on their use, they might modify the data bundle with the request or not. They act as a firewall, help you access restricted data, or even restrict you from accessing certain information. They have a lot of applications.

How a Proxy Work?
The working principle of a proxy is simple if you aren’t going deep into the technicalities involved. As I stated in the definition, a proxy is a server that acts as a gateway between you and the Internet. Why do we need them in the first place? While there are many reasons, the major ones can be summed up to data security.
When you are not using a proxy, requests you send to websites go to the websites directly. However, when you are making use of a proxy, the situation is different. When you send a request, it goes to the proxy server first which then modifies it (if it has to like substituting your real IP Address with another) then sends the request to the website on your behave. The response will be sent to the proxy and in turn, it sends the response back to you.
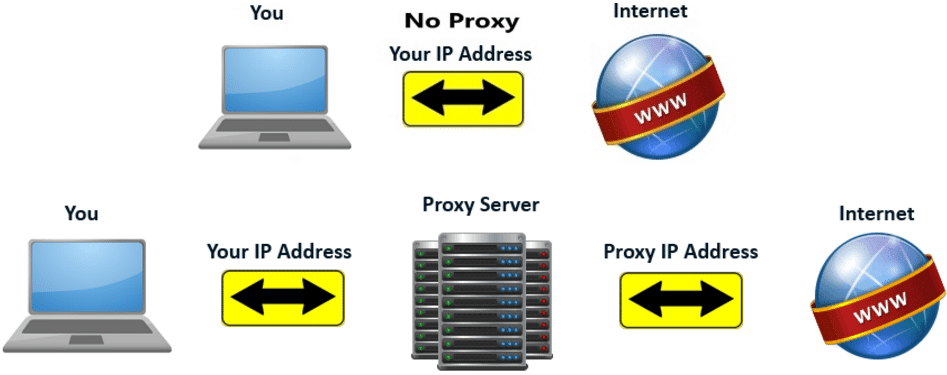
With this setup and the mode of operation of proxies, your computer can be completely shielded and hidden from the website you are accessing since your computer is not the one sending the request to it.
Proxies allow you to access the Internet from locations you have not visited before and access their local data. While it has many benefits, make no mistake about it – it also has its own shortcomings. Since proxy servers can access the information sent through them, they can, in turn, alter the data and in some cases, become the mode in which Internet censorship is achieved.
Common proxy servers
Proxies have types, depending on the mode of classification. The criteria can be level of anonymity, the number of people using the proxy, Internet protocol type, and IP source. You need to know the types of proxies available so that when trying to make a purchase, you know what you need and what you are about to purchase. Let take a look at the types of proxies based on the different criteria for classification.
<Number of Users>
Public Proxy
Public Proxies are the type of proxies that assigned many people to a single IP Address. This means that many users sometimes, hundreds of users make use of the same IP Address.
This means that if one of the users spam a particular website with it and it gets blacklisted, all the users of that blacklisted IP Address will be affected. They are mostly provided by the free proxy provider and I would advise against using them.
Semi-Dedicated Proxy
Semi-dedicated Proxy is also known as a shared proxy, just like Public Proxies. the only difference is that only a few numbers of people are assigned to an IP Address. The number is usually 3 per IP and as such, it is better to Public Proxies that will allow hundreds of users.
Private Proxy
Private Proxies are also known as Dedicated Proxies. A private proxy is named private because it is assigned only to a single user and only that person can use it – except he shares his authentication details. They are the best type of proxy. However, they are expensive. Unlike in Semi-Dedicated Proxies that the cost is shared among the users, for Private Proxies, only you bear the cost.
<IP Address Source>
Datacenter Proxy
A datacenter Proxy is a type of proxy that assigns IPs provided by datacenter to its client. They are more susceptible to detection and subsequent block as they are more associated with spam and generating them is easier. Providers of these types of proxies provide them with unlimited bandwidth and they are generally cheaper.
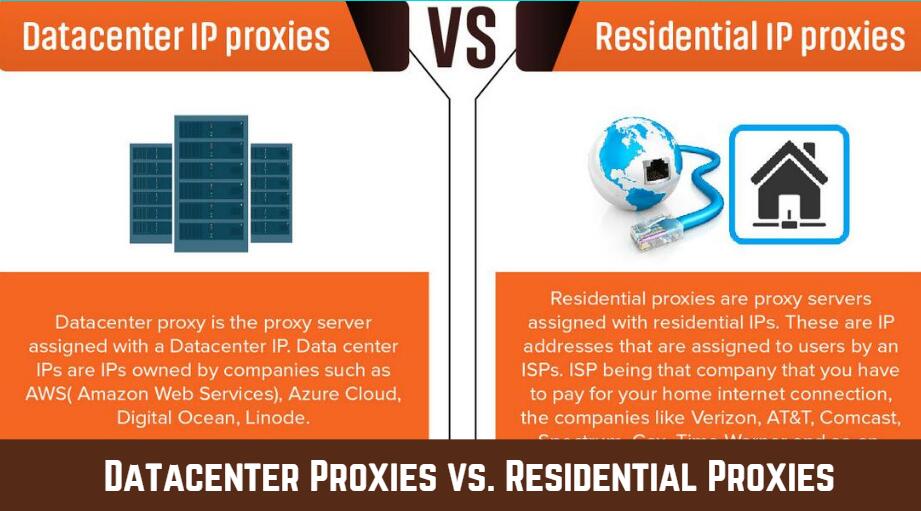
Residential Proxy
Residential Proxies are the types of proxies that route client requests through real Internet-enabled devices in people’s homes. Because they make use of the IP Addresses of these devices, they are usually difficult to detect, and as such, the cases of blocks are reduced. They are expensive and usually come with limited bandwidth.
Mobile Proxy
Mobile Proxies are the most expensive of the three types of proxies when classified based on IP addresses used. The IP Addresses used are that of mobile devices and as such, they are percent for use when you need to emulate sending requests from mobile devices.
They are, however, the most expensive and do not get blocked because of the way Mobile Network Operators (MNOs) the ISP of the devices assign IP – IP Addresses are dynamically assigned and changed after a while.
<Internet Protocol>
HTTP Proxy
An HTTPS Proxy is built on the client and server communication model. The working principle is simple – the client computer sends a request to the server and the server process the request and sends back a response. HTTP Proxies are the most common types of proxies in use today and most proxy services provide them. As an Internet user, most of the links you use are HTTPS. There is a variant to this which is the HTTP.
Different type of HTTP proxies Distinguish by Level of Anonymity
A Transparent Proxy Server is a proxy server that does not modify requests sent through it. The website you want to access will still have access to your IP Address as it does not modify your IP. They are mostly used for Internet censorship and filtering web content. They are mostly used in working environments, schools, and even homes.
Unlike in the case of Transparent Proxy Servers, Anonymous Proxy Servers modify the request by stripping out your IP Address and substitute it with its own IP Address and identify itself as a proxy to the website. This makes it difficult for eavesdroppers to know who is behind a particular web request. However, because they identify themselves as proxies, they easily get banned.
-
Distorting Proxy
Distorting Proxies are very much like Anonymous Proxies. they change your IP Address and show themselves to the websites as proxies. the major difference between Distorting Proxies and Anonymous Proxies is that while Anonymous Proxies use their own IP Address, Distorting Proxies makes use of a fake random IP Address.
High Anonymity Proxies are also known as Elite Proxies. They do not really have much difference with the Anonymous Proxies. The major difference between them is that they are usually not blacklisted and do not easily get detected as proxies as the anonymous ones get detected, and as such, they do not get blocked. They are the best types of proxies to use to evade Internet censorship and access local and restricted web content.
SOCKS Proxy
While HTTPS is the most common type of proxies, SOCKS is the default type of Internet protocol. It is basic and establishes a TCP connection with another server on the client’s behalf. The connection established is used for routing traffic between client and server.
So, all socks proxies are high anonymity Proxies, No need to worry your IP leak when you using a socks proxy.
Before are all the Different Types of forwarding Proxy servers, If you want to know more about Reverse Proxy, Go this article is an ultimate guide to Reverse Proxy server.
More, Differences Between a Reverse Proxy and a Forward Proxy
Proxy Server Vs. VPN
Aside from proxies, the use of Virtual Private Network (VPN) is also one of the popular ways of evading Internet censorship and accessing restricted/local content. What differentiates a VPN from proxy? These will be discussed below.
The major difference between proxy servers and VPN is that VPNs are installed on the computer or mobile and provide system-level protection and functionalities while proxies are functional at the application level.
This means that once VPN is activated, your Internet access regardless of the software you use will be subjected to the protection provided by a VPN. For proxies, you have to configure it on specific applications and software for them to work.
VPN have your data encrypted while, in the case of most proxies, they do not get them encrypted. However, VPNs are slower in terms of speed compared to proxies. It might interest you to know that VPN makes use of proxy servers in the background and can be said to be an upgraded version of proxy servers.
Read more,
Conclusion
Now that you know what proxies are, what next? While you might want to go and buy from any provider, I will advise against doing that. Instead, I will advise you to read our proxy buying guide so you know all you need to know so you’ll be making an informed buying decision.
Related,






