Tor is an interesting concept. The idea of layered connection bouncing through an anonymized network with semi-random exit nodes is a good one, when it comes to security. You essentially put a cloud in the way of anyone trying to track your traffic. You enter it and they have no idea where you exit. At least, that’s the theory.
Tor is not without its issues, though. It’s slow, much slower than using the Internet normally, or even through a single proxy server. It’s also not quite as anonymous as people would like to think it is. There have been a lot of big raids from the FBI, the NSA, Europol, and other law enforcement agencies. It’s not really all that secure.
If all someone needs to track you down using Tor is the ability to force you to download a large file and the ability to monitor some data, they can see both the entry and exit points and ignore Tor’s routing completely. You essentially slow down your internet connection for no practical benefit. The attacker – be they a hacker or the FBI – can just put together 1 and 1 to get 2.
The key components to this circumvention of the anonymity of Tor require two things.
First, it requires the connection entering the entry node to be yours.
Second, it requires you to be visiting a site controlled by a malicious actor. It could be an FBI honeypot or a hacker setup designed to harvest data for later sale.
On the normal web, you can just make sure not to browse websites you don’t trust. On the deep web, sites don’t have those reputations, or those reputations can be seeded and falsified. You have much less ability to avoid sites you don’t trust when the entire purpose of what you’re doing is visiting the seedy underbelly of the internet.
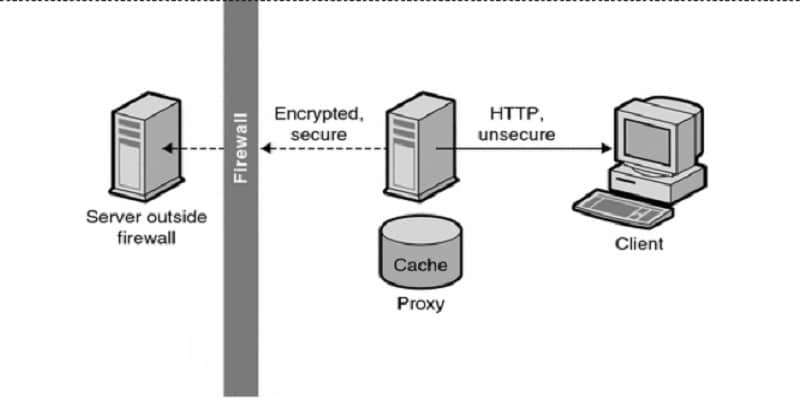
If you can’t ensure the quality of the reputation of the site you’re reaching from the exit node, you have to ensure the anonymity of the traffic you’re sending into the entry node. You can do this by layering in a level of proxy connection.
Of course, a proxy server isn’t exactly anonymous either. You have to be just as sure of the proxy you’re using as you would be of the exit site you’re reaching normally. Generally, this means that public proxy lists are out, and you have to be confident in the quality of the private proxy lists you’re using.
Achieving true anonymity is difficult. That’s by design. Governments want to be aware of what communications are happening, to avoid terrorist plots and foil uprisings. It’s no different than any system implemented for the security of something larger.
However, some degree of anonymity is necessary to keep governments from getting too oppressive. China’s Great Firewall is security gone too far, and something like a proxied Tor connection can help circumvent that kind of oppression.
I’m saying this to remind you that the issue isn’t black and white. There are terrorists using anonymous internet setups to plot. There are governments seeking them out to protect citizens.
There are criminals using Tor to buy drugs and weapons. There are law enforcement agencies preventing crime by tracking them down. There are activists using anonymous traffic to plan rallies and build support. There are oppressive regimes tracing their traffic to stomp them out, arrest them, or even kill them.
I’m not here to judge why you would want to use proxies with Tor to anonymize your traffic. I’m just here to help you do it.
Tor Vs Proxies
If Tor is designed to obfuscate the middle between your computer and a client, and a proxy server is designed to obfuscate the middle between your computer and a client, what’s the difference between them?
A proxy server is a single server that is set up to refer traffic coming into its intended destination, stripping it of referral information and replacing it with its own. This can be used to change your apparent geographic location, web browser, client version, and other details.
The problem is, a proxy server is a single server. Anyone capable of accessing it can install monitoring software, which can keep logs and piece 1 and 1 together. The proxy server knows who you are, and can be the subject of a man in the middle attack.
Tor is like using a layer of semi-randomized proxy servers. You have a designated entry node, that changes periodically. You have a randomly chosen exit node, that passes your request to your actual destination.
In the middle, you have a number of different jumps and servers, chosen randomly from a swarm. There might be 50 servers there, and you pass through 4 of them. Each time you connect, you pass through different internal nodes and come out through a different exit node. Along the way, your traffic is not monitored or modified.
It’s encrypted and untraced.
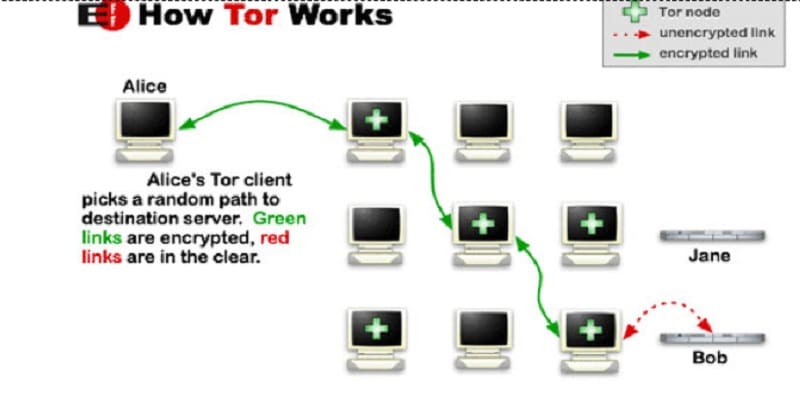
The idea is that even if one of the servers is a bad server, it just sees a proxy on either end, neither of which pass more information about you.
All the monitor would see is that the traffic is encrypted using Tor, and that’s not in itself illegal or punishable. Some agencies may see it as suspicious, but there’s no way for someone at the FBI to differentiate between you using Tor to browse Wikipedia or you using Tor to buy cocaine.
Now, some people worry that Tor has a backdoor built into it. This isn’t true, despite modern attempts to force various agencies to install such backdoors.
While Tor isn’t necessarily 100% secure, compromising it involves a more sophisticated attack than just “a special key the government can use to get in.” That, or a simpler user error, like using Bittorrent.
Using a Proxy server with Tor
Adding a proxy server before the Tor entry node helps boost your anonymity and security.
It helps obfuscate your location in case anyone is monitoring the entry node and tracing traffic.
If you’ve tried to set up a proxy server with your internet connection to route it through Tor in the past, you’ll probably notice that Tor’s icon says it is disabled as soon as you enable the proxy.
That’s because Tor expects to be able to route your traffic into an entry node, but you’re forcing the traffic to go to the proxy server instead. You’re circumventing Tor to use the proxy.
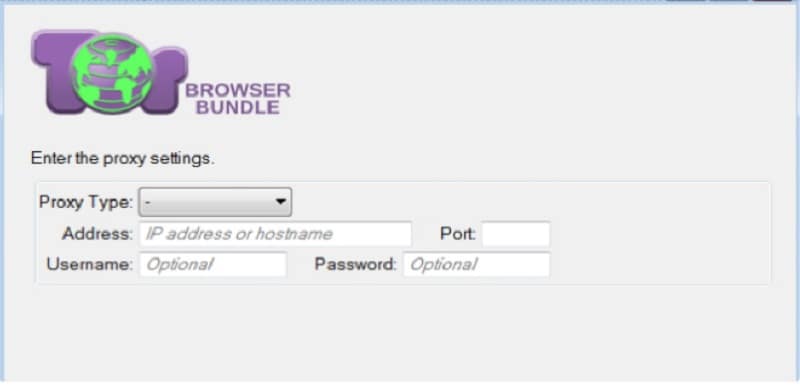
What you need to do is set up the proxy server from within Tor. Using the Tor web browser, you need to click the Tor Network Settings and click configure. The first option asks if you want to use a proxy; click yes, and you will be brought to a proxy configuration screen.
You can choose HTTP or SOCKS proxies, where you will then need to put in the IP, the password and username, or whatever other information is necessary to use the proxy. Once you have that in, click next and then click connect. If your information was correct, Tor will now be configured to use your chosen proxy server in addition to using the Tor network.
You can read a bit more about Tor proxy configuration options, including what sort of connections are required to operate Tor properly, by reading their manual page here.
Why is Everything So Slow?
The number one problem with Tor is the same problem you get on a smaller scale with proxies, and that’s slow site speed. It’s a simple matter of physics, really, and it’s not a problem that’s going to be solved.
Imagine you are standing on one end of a room and your friend is standing at the other. You have a baseball. You write a question on the baseball and toss it to your friend. They write the answer and toss it back. You get the answer, and it’s fast.
It’s not secure, though. Anyone taking a snapshot of that scene would see the originator of the traffic and the originator of the response. If they catch the baseball in the middle, they can read the traffic as well.
Now imagine you have a circle of ten friends. You write your question on the baseball, and toss it to a random person. They toss it to another, who tosses it to another, who tosses it to another, who tosses it to the friend who has the answer. That friend writes the answer down and tosses it to a random person in the circle, who tosses it to another, who tosses it to another, who tosses it to you.
Now you have your answer, but it was a lot slower. The baseball bounced between six different people, making a bunch of stops, before getting to its destination with the answer. It’s more secure, though; anyone intercepting the baseball might get the data, but they don’t know who you are or who your friend who wrote the answer is. Any snapshot only gets a minimal partial picture.
The internet works in much the same way, where each friend in the circle is a web server that is part of the Tor network. The connection has to bounce from person to person, and in some cases, it may be crossing overseas multiple times.
Tor actually makes things worse, because it’s a small network in comparison to the amount of traffic passing through it. Back to your circle of friends, imagine there are 75 baseballs flying through the air at any given time. Anyone would get overwhelmed trying to catch and throw back the baseballs quickly enough. Often several will back up and take time to be relayed. That’s what is happening to Tor to slow it further.
Adding a proxy on top will further slow your traffic, but not by much. A good web proxy isn’t going to be that much slower, particularly when it’s from a private proxy provider. Adding it on to Tor is just adding a person between you and the circle.
There will be occasional other issues with Tor. For example, using an adblocker adds a fingerprint that can be used to break your anonymity.
Google will also often glitch out; they serve content based on geographic location, so if your Tor exit node is in a foreign country, you will be served content geared for that country. It also may make you solve a captcha to prove you’re not a bot or malicious user.
Alternative Options to Tor
One option you have with Tor is, instead of using a proxy or use a VPN. A VPN can be placed either before or after your Tor connection and can add more encryption and security than a regular proxy server can provide. On the other hand, VPNs can be even slower than proxies and harder to configure.
Read More: What’s The Difference Between a Proxy and a VPN?
VPNs can be used to get around ISP blocking of Tor traffic, which has been known to happen occasionally. The VPN will be the traffic your ISP sees, and it acts as a barrier between you and your ISP.
- Bypass Blocked Websites with Private Proxies
- Why Your Proxies Are Blocked by Search Engines
- Using Proxies to Stream Netflix and YouTube From Any Country
However, VPNs don’t just cease operation if they break; in order to continue your browsing, they revert to normal traffic. This means Tor will still be visible if the VPN drops. That and a VPN is much more prone to handing over your records than a proxy server would be. This is where proxies excel.
At the end of the day, there is no truly secure, anonymous way of browsing the Internet. Whether it’s because you’re sending personal information out, or logging into accounts tied to your information through an anonymizer, it can still be compromised.
Tor, if you’re truly afraid of surveillance, is not going to be your solution. Then again, neither will a proxy, or a list of proxies. If, on the other hand, you merely want your traffic hidden but aren’t doing anything to break the law, you’re probably not going to be a target regardless.