Are you looking to learn more about bot attacks on websites? Come in now and read our comprehensive guide on what they are, how they are perpetrated, and the best way to prevent them.

Bot Attack is a significant concern in the world of tech today. Research shows that in 2020, 59.2% of website traffic was human-driven, 25.6% was bad bot attacks, and 15.2% was from good bots. Even though such records are being taken note of, it doesn’t strike out the fact that bot attacks keep skyrocketing as the day goes by.
The evolving threatening side is the advancement of this automated tool, now having attributes likened to humans. A bot can be programmed to behave like an actual human in carrying out any activities, which has seen its threat to advance by increasing percentage figures. In 2022, a report by Imperva recorded that bot attacks surged by 2.1% from the previous year to 27.7% of bad bots, and those without malicious intent or good bots dropped by 0.6% from the preceding year to 14.6%.
The message this statistic sends is that bad bot attack is taking the lead, and this will surely do no good but harm if nothing is quickly done about it. So, are there ways to prevent this Bot Attack? Of course, and that is the driving force of this article.
What is Bot Attack?
Bot Attacks are malicious behind-the-scenes activities carried out by cyber criminals or hackers using automated tools called bots. These bots are so flexible and agreeable that they can mimic the behavioral features of humans. Hence, whatever they are set up for is what they engage in. What makes this tool scary is that it is super-fast in execution, and it can carry out multiple tasks simultaneously as a botnet. i.e., several bot networks to achieve a common goal.
However, this, in turn, can damage any defenseless website to be completely vulnerable. Bot attack is not what any organization or agency should encounter as the experience pierces through the zeal of your brand. Because it is tacky to those launching its attack, hundreds of websites are unleashing on. As of 2022, findings by Imperva report that evasive bots are on the rise; by percentage, they are 65.3% among all bad bots.

These bot attacks can be targeted to your website and evade its anti-spam system causing tremendous damage. The threat from this automated tool is not something to perceive and handle with levity, as its usage can drain and nail a company down to zero. There are lots of cyber threats cybercriminals send forward, and it is mainly done by bots because, since bots can emulate human behavior, they are difficult to spot.
Types of Bot Attacks
Bot attack comes in different forms, and understanding them is crucial. It prepares you, as a brand owner or an organization, to know what you are against. Although no bot attacks should not be given keen attention, they are of priority based on the damage they can cause. While some bots can be flexible, others appear invincible. Now, let’s see the varieties of these bot attacks.
-
Botnet attacks
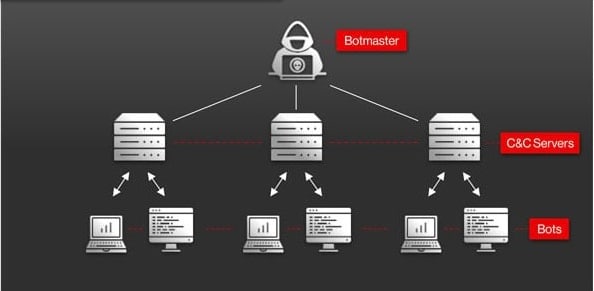
A Botnet attack is when several infected zombie computers are used to attack a web property. These computers have bots installed on them. the bots come together to accomplish multiple or large attacks. Hackers are the brain behind these attacks, and botnets provide them with multiple computer resources that they wouldn’t have had access to, including hundreds of thousands of IP addresses. The devices used are without the consent of their respective owners since they are infected with malware.
-
Sophisticated Bot Attacks
Sophisticated bot attack advancement has made bots be likened to human behaviors. Bot activities are also significant when talking about the methodology of cybercriminals, and as a result, bots have 77% participation in cyber threats and attacks. A sophisticated bot attack is not merely like other bot attacks that can easily be fished out. It raises lots of alarm because it is highly malicious, and when it manipulates its way into any website or brand, you will not be able to spot or detect it, yet it’s causing lots of damage.
-
Phishing attacks

Phishing is another type of bot attack that is crucial and maliciously done by cyber attackers. When a cybercriminal intent to raid a website and retrieve personal information from users, knowing it will not be easily possible, as such, this method of a bot attack is used. It works by using social engineering tricks to lure users into letting out their personal information and username and password.
For instance, a hacker can send an email through the website of a trusted brand, and the individual involved can see this as legitimate and respond to the mail with whatever information they request. By doing that, you have unknowingly given accessibility and authority of your privacy to unworthy unauthorized attacks with detrimental value. The first phishing attack was in the 1990s, and there are several types of this attack.
-
DDoS attacks
DDos is an abbreviation that represents Distribution Denial-of-Service. This type of bot attack is achievable when the attacker keeps sending in web traffic or engaging in the activities of a target company using hundreds and thousands of bots to send in this request in sync.
However, this request will be forwarded to over-exhaust the website so real visitors wouldn't recognize the site. As of 2020, DDoS attacks have skyrocketed due to the pandemic.
Additionally, concerning a report from NETSCOUT, during the COVID-19 lockdown, over 10 million DDoS attacks were sent, targeting many of the remote and essential services individuals were using to survive through the lockdown.
-
Brute force attack

Brute force attack, as the name implies, means hackers are forcing their way to gain access to your personal information and account. Cyber attackers engage in brute force attacks by a mere try-and-error cybercriminal method. They try everything out of anything to get their way through. The strategy will be to try any alphanumeric key combination that matches their precise target authorization key.
Your login details are yet another lead they try to guess, and other encryption keys they can decrypt to have their way. Although this is common, its success rate is low. If you have a solid key combination, no one can access your privacy except you, but otherwise, it is a game changer for them and a considerable loss for your company.
Some people can refer to this as credential stuffing or Account Takeover (ATO). According to recorded statistics, 0.1% of these attacks often result in a successful login.
More Types
-
Spamming
Botnets can be used to send massive amounts of spam emails, flooding the inboxes of unsuspecting users with unwanted and often harmful messages.
-
Click Fraud:
Click fraud is when bots are used to artificially inflate the number of clicks on a specific advertisement or website. This type of attack can cost advertisers significant amounts of money and can also harm the reputation of the targeted website.
-
Ad Fraud:
Ad fraud involves the use of bots to generate fake impressions and clicks on online advertisements. Advertisers pay for these fake interactions, resulting in significant losses for both the advertisers and the owners of the targeted websites.
-
Data Scraping:
Botnets can be used to scrape websites for valuable data, such as email addresses, phone numbers, and financial information. The information collected can then be sold on the black market or used for malicious purposes.
There are some legitimate uses of botnets such as data scraping or data collection for research purposes. Companies like BrightData and Soax offer web scraping services, which are used to gather data from websites for various purposes, including market research, price comparison, and content scraping. These botnets are designed to perform specific tasks within a set of rules and regulations set by the website owners.
-
Information Theft:
Botnets can also be used to steal sensitive information, such as login credentials and financial information, from websites and computer systems. This type of attack can result in identity theft and financial loss for individuals and organizations.
-
Vulnerability Scanning:
Botnets can be used to scan websites and computer systems for vulnerabilities, making it easier for cybercriminals to launch attacks and gain unauthorized access.
These are just a few examples of bot attacks. It is important for individuals and organizations to be aware of the different types of bot attacks and to implement security measures to protect their online assets.
How Do Bot Attacks Work
Typically, bot attacks follow four (4) primary steps or processes. These steps are the general stages, meaning that the individual and the steps will further differ by the type of bot attack the hacker wants to initiate. Now, let’s understand what these four stages are.
1. Reconnaissance
In the Reconnaissance stage of a bot attack, the hackers scout, inspect, investigate and explore the target website they intend to have a go at. They can even purchase or subscribe to tools or software that can foster the website or users' credentials they are after.
2. Setup
Setting up the activities content is the next in line. In this stage, attackers schedule and plan how the process of its target is going to be, which method to be adopted, at what speed, when it should forgo the command and the automation process, and whether it should be automatic or not.
3. Attack
This stage is where the attacker initiates the attack to see how it goes and what works and what doesn’t. The duration set matters a lot, and after everything has been put up, the attack will start, and it may take days, months, or years, depending on the structure and pattern you wish to use. Attackers can set new rules and engagement as they learn to know the site environment.
4. Outcome
To wrap up this section is the outcome. Here the attacker tries to acquire the credentials he has planned, using any means of bot attacks, either DDoS, brut, phishing or among others. The outcome speaks louder, so whatever comes out of it is the determinant of whether or not the criminal will push further, try again, use a sophisticated bot to advance more, or readjust to make multiple attacks.
Examples of Bot Attack
With the understanding of the types of bot attacks, there are examples to show in addition to other activities where bot attacks can arise. So let's see what other malicious motives cybercriminals can also use bots to automate.
1. Web Scraping Attacks
Web scraping is collecting, extracting or gathering data from another user or company’s webpage. Web scraping is never perceived as ethical unless the search engine does that to crawl and scan content. However, with the usage of bots, scraping is always of specific intent. Hackers program bots to gather data, and the bot automatically collects this data by copying and pasting the data from another website of the hacker’s interest.
2. Ticketing Attack
Event tickets are another excellent example of a bot attack. Buying and the of sales ticket has become a business many event centers carries out. To purchase tickets of hundreds and thousands of gate pass legitimately is often not possible – as the process of doing this is tedious and strength wrecking; hence, why ticketing bot usage becomes paramount.
The more tickets you acquire and resell, the more money you earn. With an automated bot, cyber fraudsters can buy all these tickets with a round, and the scalper resells them for a higher value. The ticket we are talking about is mostly concert tickets.
3. Credit Card Attacks

Credit card bot attack is one crucial area bot usage is dealing with normal users. Fraudsters' bot usage has seen to rise the vulnerability of what is supposed to be personal. There is a strategy in bot usage known as card cracking. The process involves the use of software or a bot to automate activities on the internet.
Fraudster has internet users believe that they can create a private account online. On doing that, they will have the privilege to extract your card details, and if they can’t get all your information, they will guess it and use your credit card.
It will interest you that not only one account but multiple accounts can also experience this crack, and money will be stolen. Additionally, buying private account numbers on the dark web can result in these fraudulent acts. Adding a device to a credit card and phishing, among others, can cause bot attacks.
4. Inventory Denial Attack
Inventory bot performs a similar function as a ticketing bot. However, what differentiates this two is the fact that fraudsters don’t have the intent of buying all. They engage in the purchase to know the price as resellers to enable skyrocketing costs to their benefits.
Sometimes, they compete to purchase this bot to help a competitor. What’s the catch is that they understand what the current price is, and that can help them. Inventory Denial Attack is also seen as a sneaker bot.
Dangers of Bot Attack
The pressing dangers of bot increases as the advancement of this tool also evolves. Hence it is crucial to know the alarming risks of bot attacks. In this section, we will list some of the dangers of bot attacks.
- Security breach and data theft in organization
- Bot attacks lead to malware, thus resulting in the corruption of files.
- Bot attacks cause companies' legitimacy and legacy to undergo serious questioning and scrutiny. As such, forcing the company to face legal issues.
- Finance losses are something bot attack has triggered over time. Many businesses have lost hugely due to bot attacks.
- Bot attacks diminish an organization's site visit, depriving them of real users’ webpage traffic.
- Since bots can imitate human attributes, they can sit on top of website growth. i.e., They can prevent any website or company from having the incredible growth it should have. The process is oppressive – as it can completely shut a brand website off its ranking page and can also bring down a company to zero.
A cheat sheet for preventing bot attacks (10 Tips)
Use a reputable Web Application Firewall (WAF)
A WAF can help detect and block bot traffic before it reaches your website, However, even the best WAFs such as Cloudflare and Akamai can be bypassed by determined attackers, who may use techniques such as IP spoofing or evading detection by sending encrypted traffic.
Enable IP blocking
Block IP addresses that are known to be associated with malicious bots. However, some bots can bypass IP blocking by using residential proxy networks. This makes it difficult for organizations to block IP addresses associated with bot traffic. To counteract this, organizations can use a more sophisticated method of IP blocking, such as geolocation-based IP blocking or user-agent blocking.
Geolocation-based IP blocking involves blocking IP addresses based on their geographic location, while user-agent blocking involves blocking IP addresses based on the user-agent string they provide when accessing your website. This makes it easier to distinguish between legitimate and malicious traffic, and to block malicious traffic before it reaches your website.
It's important to note that while IP blocking is a useful tool in the fight against bot traffic, it should not be relied upon as the sole method of protection. Instead, organizations should use a combination of techniques, such as IP blocking, CAPTCHA, and a WAF, to provide a comprehensive defense against bot attacks.
Use CAPTCHA
CAPTCHA is a technique that can distinguish between human and bot traffic. By requiring a user to complete a task, like entering a code or solving a puzzle, you can ensure that only humans are accessing your site.
However, it is not foolproof. There are various ways that hackers can bypass CAPTCHA, including using Optical Character Recognition (OCR) technology, exploiting weaknesses in the CAPTCHA implementation, or using bots specifically designed to solve CAPTCHAs.
To stay ahead of these threats, it's important to use CAPTCHA in conjunction with other security measures, like a WAF, and to regularly review and update your CAPTCHA implementation to address known vulnerabilities. Additionally, implementing a multi-layer approach, such as using both traditional text-based CAPTCHAs and more advanced forms of CAPTCHA, like reCAPTCHA, can help make it more difficult for hackers to bypass your security measures.
Implement rate limiting
Limit the number of requests a user can make within a specific time frame to prevent bots from overwhelming your website.
Monitor traffic patterns
Regularly monitor your website traffic to detect any unusual spikes in bot activity.
Keep your software up to date
Regularly update your website software, including your CMS, plugins, and themes, to protect against known vulnerabilities.
Educate your users
Educate your users about the dangers of bot attacks and the importance of using strong passwords and being wary of suspicious links or emails.
Use multi-factor authentication
Require users to provide multiple forms of authentication, such as a password and a one-time code sent to their phone, to access sensitive information.
Implement security measures on your server
Secure your server by implementing measures such as firewalls, intrusion detection systems, and vulnerability scanning.
Work with a security consultant
Consider working with a security consultant to perform regular security audits and ensure that your website is fully protected against bot attacks.
How to Prevent Bot Attacks for non-technical
There are different ways to prevent this bot attack, and in this section, we will be diving right into some.
-
Keep a Healthy Cybersecurity Routine

Preventing your company from bot attacks is not a day job. While you may feel there are tools to see you through, if you don’t come correct with this malicious act, it won’t kick itself off. Maintaining a good cybersecurity routine is one way to set your company one step above this bot attack issue. Be involved in several strategic security practices, and ensure your employees are well trained or undergoing training on cybersecurity measures.
Protect your company’s credentials by cracking out an unbreakable password. Don't give access to any user without understanding their intent and security strength because bots are more strengthen than you could imagine. Essentially, your username can stand the test of time, but once your key combination that serves as a password is hijacked, and you grant access, the damages will be unpleasant.
-
Updated System
Device up-to-date is also a determinant to preventing attacks. One thing you should always understand about bot attacks is that humans are behind its instructions, and how they program this bot to carry out their activities is in line with how vulnerable your system is. Therefore, it is a must that you keep your systems current.
Update regularly so long these updates are available and keep the activeness of the systems going. Do not say because a particular feature is of no use, you shouldn’t update it. Remember that what you fail to do will be the one to mar you. So ensure you install every update.
-
Constant Monitoring of Network Traffic
To monitor your network traffic, knowing the source is very crucial and requires you to be able to detect where and how your site generates its traffic. Analytical tools can come to play here to help foster constant and continuous monitoring. The growth of your brand invasion to bot attack lies in the way you handle this aspect very well, so be sure to use this analytical tool, because it can reveal to you all that is important, right from the traffic coming to your site down to the malicious data outflow from your site.
-
Initiate Control Access
Gaining control access to your system will help you to know and detect where these bot attacks are coming from to enable you the privilege to flush them out. To do this does not only deals with your alphanumeric key combinations, i.e., password. Separate your system from each other, so you can initiate a two-step or multi-factor authentication to fish out unauthorized users.
-
Outsource to Third-Party Tool
This point is about using the professional companies you know to render the prevention of the said bot attack. You need to pay for their service, and they will help with the complete protection of your website. This method is not new, but making sure to outsource to a company with good and honest credibility is very important. Some companies are hackers themselves, so if you do not do your homework well, you will quickly fall victim. And this, in turn, will cause damage to your brand.
FAQs About Bot Attacks
Q. What Are Botkits?
Botkits is any software development kit (SDK) that allows the customization and creation of a bot. It is often open source. Botkits are flexible; in essence, they give the upper hand to cybercriminals to carry out their work effectively.
Note that this tool is of no use to the company, cyber attackers pay or install it for free, and its harms have yielded the terrible activities of the bot attackers. Many other tools like this will help foster the criminal act and make bot attacks more rigorous for companies.
Q. Is Bot Attacks and Botnet Attacks the Same?
Although they have the same context, what they do is slightly different. A bot attack is a process of using bots to carry out malicious tasks on target sites. There are many ways bot attacks can be carried out, including the use of a botnet or a single bot.
A botnet takes advantage of the network effect. A good number of bot networks on infected computers carry out a single task with the aim of multiplying all of their minute effects into a devastating one.
Conclusion
Bot attacks have become so resounding that their negativity can pull down an entire empire. If no action is taken to battle its destructive act and invasions, in no time, the legitimacy of websites will yield nothing but bot traffic. So, having done thorough research, we have come up with a comprehensive knowledge coverage on what bot attack is, the types aligning with several examples, the dangers of it, as well as preventive measures. Beware of Bot Attacks.






