What do you know about botnets? If you know little to nothing, then the article below has been written for you. Read the article to understand the fundamentals of botnets.

In the heat of the dwindling world economy and the simultaneous advancement in technology, cybercrime has done nothing but increase. Across different nations and continents, individuals and businesses still experience cyber attacks regularly. There are quite a number of reasons why cyber criminals attack websites and embed malware into legitimate applications.
It may be to access an individual or company's financial details, sensitive personal data, IT services, and infrastructure make a social or political point, conduct fraudulent activities, and espionage, among many other reasons.
To commit large-scale cybercrimes, these criminals make use of something known as a “botnet”. To succeed in these attacks, cybercriminals, fraudsters, and hackers make use of botnets to accomplish their malicious agenda. A botnet, among many others, consists of a cyber criminal known as a botmaster.
This individual is in charge of running a number of command and control systems. Attacks by botnets are becoming more frequent. Cybercrime groups leverage it to send spam, bombard websites with Dedicated Denial of service (DDoS) attacks, etc.
In this post, we are going to discuss the basics of what a botnet is, how they work, and how criminals take advantage of them for their bad intentions on the internet.
What is a Botnet?

The phrases “robot” and “network” are combined to generate the term “botnet.” Thus, a botnet is a collection of infected computers or other internet-connected devices that cybercriminals employ to carry out various cyberattacks, including the spread of malware, the sending of phishing emails, the crash of servers, and so forth.
Botnets can also be referred to as networks of hacked computers and gadgets. However, bots are computer programs that use each and every machine in the network to execute automated scripts. A “bot master” or “bot-herder” is someone who manages and maintains a botnet.
Infected devices can receive updates and alter their behavior instantly since botnets are still under the control of a remote attacker. As a result, bot-herders frequently have the ability to rent out access to certain areas of their botnet on the black market for a sizable profit.
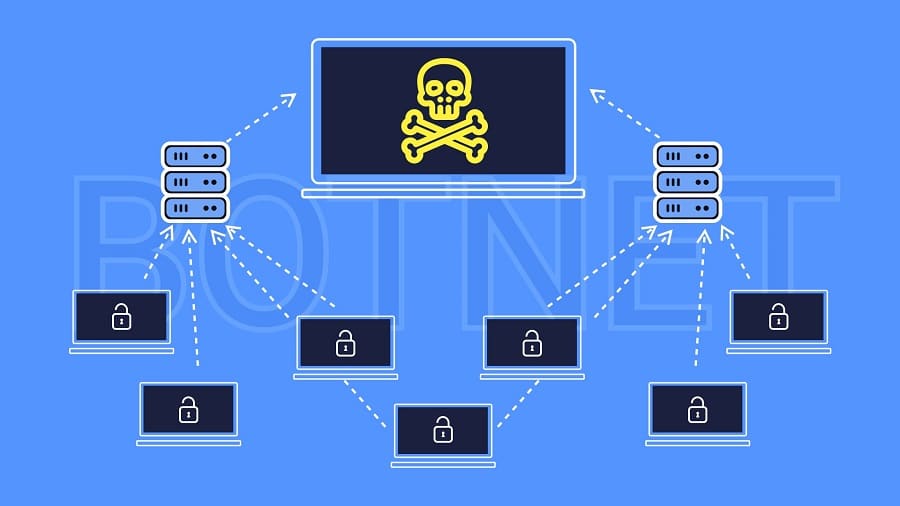
Since botnets can carry out numerous essential and repetitive tasks, such as managing chat rooms, keeping track of points earned during online games, expanding, automating, and accelerating operations by gaining access to more resources from users, etc., they may not be harmful to the network on their own.
Unfortunately, the phrase “botnet” carries a negative meaning because malicious individuals frequently employ the technology for their own gain.
How Does Botnet Work?
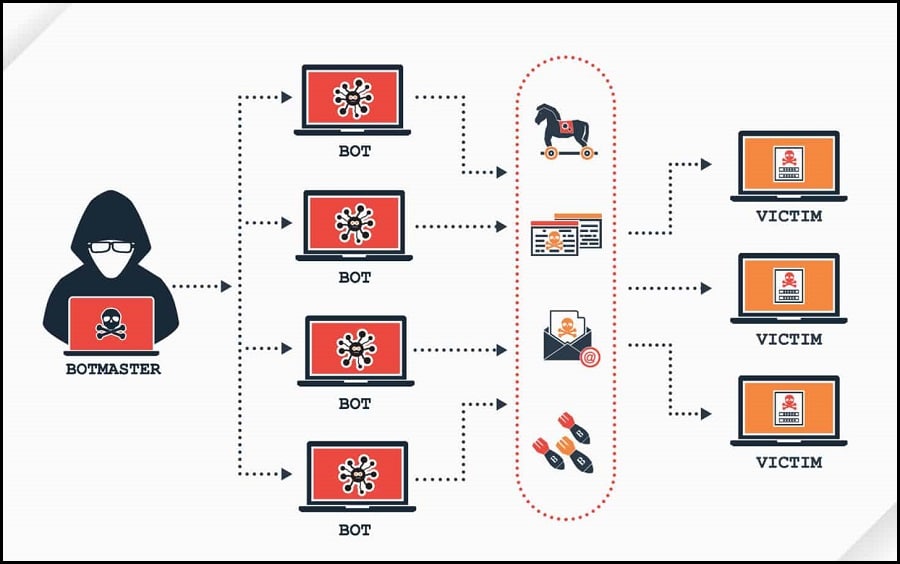
Having discussed botnets, let's examine how they work. To understand how botnets work, we need to explore the 3 basic stages of building a botnet.
The 3 basic stages of building botnets are as follows:
Stage 1: Prepare and Explore
In this phase, the hacker takes advantage of a vulnerability to infect victims with malware. By doing this, the hacker creates a setup that will entice the target to unwittingly or consciously expose themselves to malware. Hackers frequently use software or website security flaws to their advantage. Through emails and other online messages, they can also haphazardly distribute the malware.
Stage 2: Infect
The devices of the users are then infected with malware that can take control of their device once the hacker or cybercriminal has investigated the vulnerability of a website or piece of software. The malware is injected to make the end user device's security to be compromised.
Many of the techniques used either entail convincing users to download a certain Trojan infection using social engineering or when a user visits an infected website.
Other attackers may be more aggressive by employing a drive-by download approach. Eventually, cybercriminals eventually manage to compromise the security of many users' computers and gadgets, regardless of the technique used.
Stage 3: Activate
Taking control of each device is the last step in how botnets operate. When ready, the hacker groups all of the compromised computers into a network of “bots” that they can control from a distance. The successful activation of the botnet gives the online criminals access to read or write any data stored in the system, collect any personal information, share the data from the targeted devices, and also keep track of all activity taking place on the targeted device.
Types of Botnets
When a hacker or fraudster has control over a botnet, several dangerous scenarios are possible. Many different kinds of assaults can be carried out via a botnet. Following are some of the main and frequent botnet attack types:
-
Distributed Denial-of-Service (DDoS)
In a Distributed Denial-of-Service (DDoS) attack, a botnet floods a targeted server or application with requests in an effort to crash it. It is commonly referred to as a volumetric attack. The numerous compromised computer systems or devices in the network that are employed to produce this unsettling traffic provide this form of botnet attack its effectiveness.
Computers, Internet of Things (IoT) gadgets, and other data-driven devices may be among these gadgets. On the flip side, a DDoS assault can mimic a traffic bottleneck that has been purposefully set up to prevent the intended end users from getting where they need to go.
-
Phishing
One of the most common botnet attacks is phishing. Hackers and cybercriminals assume convincing identities in order to trick their victims into disclosing sensitive information such as passwords, social media login information, and banking login information. Because botnets are automated and contain numerous bots, stopping a phishing effort is similar to playing Whack-A-Mole. They frequently contain significant amounts of spamming.
-
Spam-bots
A spam bot is a botnet that is an automatic software program. In a spam bot attack, botnets are utilized to send out massive amounts of spam messages. This allows cybercriminals to send out large numbers of phishing emails with just one click. With spam bots, thousands of emails can be sent in a matter of minutes.
Hence, the emails to which the spam messages are sent are harvested from websites, chat rooms, forums, and any other places users enter their email addresses. Over 80% of spam messages are assumed to come from botnets.
-
Brute Force Attack
Brute force attacks, in which specially created programs are used to forcefully break web accounts, are another type of botnet attack. More than 5% of all security breaches are known to have been brought on by it.
Threat actors attempt different combinations of the users' login information until they succeed in accessing the targeted system without authorization. In this type of botnet assault, “Hit and Trial approach” is used. To accomplish the operation, however, several brute force attack tools are used.
How to Make Botnets/ How Botnets Are Created
Botnets are created basically by infecting a large number of computers with malware and turning them into slave computers for the bot-herder. This malware can infiltrate a computer system in a number of ways, such as a trojan inside an email attachment, a web browser vulnerability, or drive-by downloads.
We have discussed in a previous session how botnets are built. However, there are a few platforms or software that can aid in the process of creating a botnet. As such, we would like to give a disclaimer here that we are in no way supporting malicious botnet attacks with the information in this session.
The “BYOB” platform is an excellent example of a botnet creation platform (Build Your Own Botnet). “BYOB” (Build Your Own Botnet) is a framework that incorporates every component needed to build a botnet. It is an open-source project that offers developers and security experts a framework for creating and managing a simple botnet.
You could enhance your ability to design malware countermeasures with the aid of this framework. We can use Netcat, an open-source TCP server, as the master server. Despite having nothing to do with botnets, Netcat is a practical and well-known tool that can be utilized during the establishment of a botnet.
Zeus Code, ICE-9 (Ice XI), Citadel, SpyEy, and Neutrino are more platforms that can be used but may necessitate some sort of financial commitment for botnet creation. These can be found on the dark web as well.
You may be like to read,
- Honeygain Review: Is It Legit & Safe to Share Your Internet connection?
- Honeygain Vs IPRoyal Pawns Vs PacketStream Vs Peer2Profit (for Passive Income)
- Luminati: Everything You Need to Know & How to Use Luminati Proxy
- Hola Alternatives: 10 REALLY FREE VPNs Similar to Hola VPN
How Much Do Botnets Sell For?

Because many botnet attacks have legal repercussions, cybercriminals are constantly figuring out ways to remain anonymous. This is a key factor in why many of these dishonest people use proxies. Some proxies, particularly residential proxies, first heard? learn guide about residential proxy here, encourage the use of botnets. Due to their legitimacy, they are used by cybercriminals.
- 15 Rsocks Alternatives (Rsocks has been seized for botnet)
- 911.re Down! 911 Proxy was Permanently Closed. Why?
Devices used in botnets may be accessed by proxy providers. Researchers identified the kind of devices that are part of a residential proxy network using active fingerprinting techniques. They discovered that certain devices had fingerprints connected to webcams or Internet of Things (IoT) devices, where user agreement to join a proxy network is not feasible.
Therefore, the price range for a botnet's alleged residential proxies would typically cost between $10 and $500. Comparatively, small botnets of a few hundred bots are more affordable, costing an average of $0.50 per bot and costing between $200 and $700. Larger botnets are more expensive.
A 19-year-old hacker from the Netherlands built the Shadow botnet, which had over 100,000 computers in it and was offered for sale for $36,000.
How You Can Join A Botnet Unknowingly
There are quite a number of ways your device can become a member of a botnet. Many times we don't get to know because our systems keep running normally as if nothing has happened. Some of the ways you can join a Bonet unknowingly include the following.
-
Emails
An email sent to you by a cybercriminal may appear to be from your bank or credit card issuer. The email may instruct you to click on a link to prevent the termination of your service or to update your account. When you open the link, your device is flooded with malware, which enables scammers to hijack your computer and add it to their botnet network.
-
Visiting infected websites
Additionally, accessing websites that immediately download malware to your computer can unintentionally infect it. Legitimate websites are susceptible to hacking. Also, the users of those sites run the risk of unintentionally downloading malicious malware.
-
Infected file download
By downloading an infected file from the Internet, you run the risk of becoming a part of a botnet. Additionally, malware can spread through file sharing and mobile app downloads(for mobile infected devices).
How To Protect Your Devices Against Botnets?

Due to the prevalence of botnets online, you must take precautions to prevent your devices from being used for illegal activities. To fend off malware botnets:
- Downloads should only come from reliable websites and genuine, reputable sources.
- Ensure your devices have dependable virus protection and a firewall that is correctly configured to protect you from malware and bot installation.
- Install browser security as well; this will shield you against phishing websites and accidental malware downloads that go undetected.
- Update your browser regularly.
- With email attachments, exercise caution.
These and other measures will lessen the chance that malware may infiltrate your system's deeper layers and be able to make changes and run files without limitation.
Legalities to Botnets

Botnets are not always harmful. However, programmers have discovered ways to take advantage of flaws in commonly used systems to corrupt, damage, and manipulate computer networks— oftentimes without the owner or local operator of the machine's knowledge. As a result, running a botnet is prohibited and frequently punished as a criminal.
Because it is forbidden to break into computers without permission, the United States' present criminal code forbids the development of a botnet. Additionally, using botnets to commit additional crimes is forbidden.
A bipartisan group of U.S. senators reintroduced the International Cybercrime Prevention Act on June 17th, 2022. If this legislation is approved, federal prosecutors would have more resources at their disposal in the fight against cybercrime.
One justification for this measure is that present law restricts the Department of Justice's power to shut down botnets through court-ordered injunctive relief even though the U.S. is currently experiencing “a spate of severe cyberattacks.” Only when botnets are using “unlawful wiretapping or fraud” can they do so.
Although the International Cybercrime Prevention Act gives federal law enforcement more authority, the legislation ultimately offers little to change the current legal foundations for taking public and private action against botnets.
Conclusion
We have concluded that botnets may not be detrimental in and of themselves. However, they are regarded as “bad” due to the illegal actions they have been involved in. As a result, you now understand what a botnet is, what it does, and how to prevent your devices from joining the zombie army of cybercriminals' bots.