What do you know about network scanners? If you are looking forward to learning about IP and port scanners, then you’re on the right page as we will be providing you an introduction to the world of network scanners.

Internet networking has revolutionized how we communicate with each other, send files, and access data not directly on our devices. It has not only made communication between wired devices possible, but it has also made it possible for devices in remote locations not to have any form of wire connecting them to communicate effectively among themselves. This is made possible because of the Internet Protocol (IP) technology. Setting up computer networks at any scale and troubleshooting it requires network scanners.
While there are many types of scanners depending on the parameter you want to use to classify scanners; we want to discuss the IP scanners and port scanners and how they relate to networking. At the end of this article, you will not only know what IP and port scanners are, but you will also know what they are used for and how they work. You will also discover that they go hand in hand.
What are Network Scanners?

Network scanners are the tool used for network scanning. In networking, network scanning is the process of finding out all of the active devices on a network and its open ports by using features in the network protocol to ping them and wait for responses.
Network scanning is used mainly for security assessments of networks to find out and correct the vulnerability. Network scanning is also useful for system and network maintenance. However, it also remains one of the greatest tools of hackers, crackers, and other bad actors on the web that look for vulnerability in other to exploit networks.
Network scanning is not illegal. However, this does not mean you should go about scanning any network to discover the connected devices and open ports in them, as that could get you into legal trouble. Not because doing so in itself is illegal as there’s no law that makes it illegal, but the owner of the network could sue you.
-
IP Scanners

An IP scanner is a type of network scanner that scans a network finding active IP addresses, their associated devices, and other information that can be known remotely. With an IP scanner, you can detect the devices connected to any network provided the device is active and can respond to requests.
IP addresses are unique identifiers assigned to devices in a communication network for network interface identification and location addressing. What IP scanners do is that they scan a network to find out the devices that are active so that the network admin can tell whether the device can be communicated with or not.
-
Port Scanners
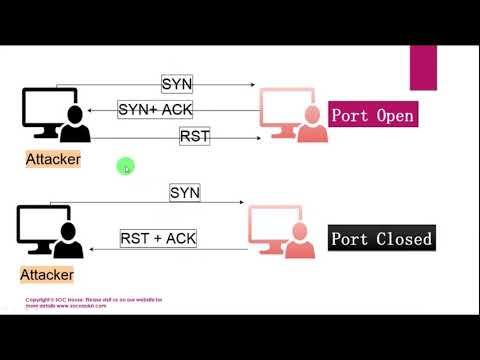
While IP scanners scan networks to detect the active devices on them, port scanners are geared towards scanning individual devices in a network to discover open ports. Devices have about 65535 ports through which you can communicate with them.
It is important you know that IP addresses only give you a direction to a device. For communication, you will need to use specific ports, and as such, you can see ports as the windows and doors through which you can enter a house, while the IP address is the address to the house.
While devices have thousands of ports, only a few are open, which are different based on the device and the type of communication allowed. Many of the ports are closed for security reasons.
Read more,
- What is a Proxy Port & How to find a Proxy Address and Port?
- How to Use a Proxy Scanner to Bulk Scan and Test Proxies for Ports and Speed
How Do Network Scanners Work?

The way IP scanners work is entirely different from port scanners. However, many network scanners do have support for both IP and port scanning, which means that you do not need two tools to scan both IPs and ports if you can get your hand on a scanner that supports both. The model of operation of network scanners is simple on the surface if you do not want to go into the technical details of how it works. Basically, all network scanners have support for setting the IP range which you want to scan. You will need to specify the network you intend to scan and then the IP range.
If you did not specify the IP range which you want to scan, the scanner would use the default setting, which is the local subnet, so all of the IPs of the local subnet would be scanned. All the scanner does is send pings to each of the IP addresses in the range which you are interested in to get details about the IP.
Some of the information IP scanners would try to find out includes if an IP address is active, the device it is assigned to, and the device-related information such as Operating System, vendor, MAC address, and the description of the device, among other details provided. If the scanner has support for scanning ports for each of the IPs/devices, it scans the individual ports to find out the status (open, close, or filtered).
All of this information is provided to you as a list by the network scanner, and you can use the filtering tool to filter the list for IPs of interest or export it in any of the file formats supported by the network scanner.
Uses of Network Scanners
Network scanners have come to stay because of their enormous importance even though they are being used by hackers and other bad actors to detect vulnerability that can be exploited in a network. Let take a look at some of the uses of network scanners below.
-
Troubleshooting Networks and Connected Devices

One of the major uses of network scanners is to troubleshoot. Network administrators use them to find out the devices connected to their network and ports open. With this tool, you can find out if a device is correctly configured and connected to the network or not. They also use it to determine the kind of communication allowed by check open ports. Without a scanner, it would be difficult for admins to detect some of these problems and provide solutions for them.
-
Security

One good use network admins can put your network scanners to is to check the devices connected to their network. They could do this constantly or at intervals to detect if any strange and unknown device has connected to the network in other to investigate and disconnect it. A network scanner is also useful for detecting vulnerability so that the vulnerability can be patched to protect it from being exploited by bad actors on the web.
-
Auditing Network

Another use network scanners are put to is to create an audit of the devices connected to the network and the ports open. While not network admins are interested in this, network auditing is very important, especially if the network is large and you can’t keep a tab on the devices easily.
How to Use Network Scanners
In this section of the article, I will be showing you how to make use of network scanners. We would be using the Angry IP Scanner as an example for this guide so that you will understand the guide better.
- Download the Angry IP Scanner from its official website. This tool is free to use and is available for Linux, Windows, and Mac. Install it and launch it to follow the guide.
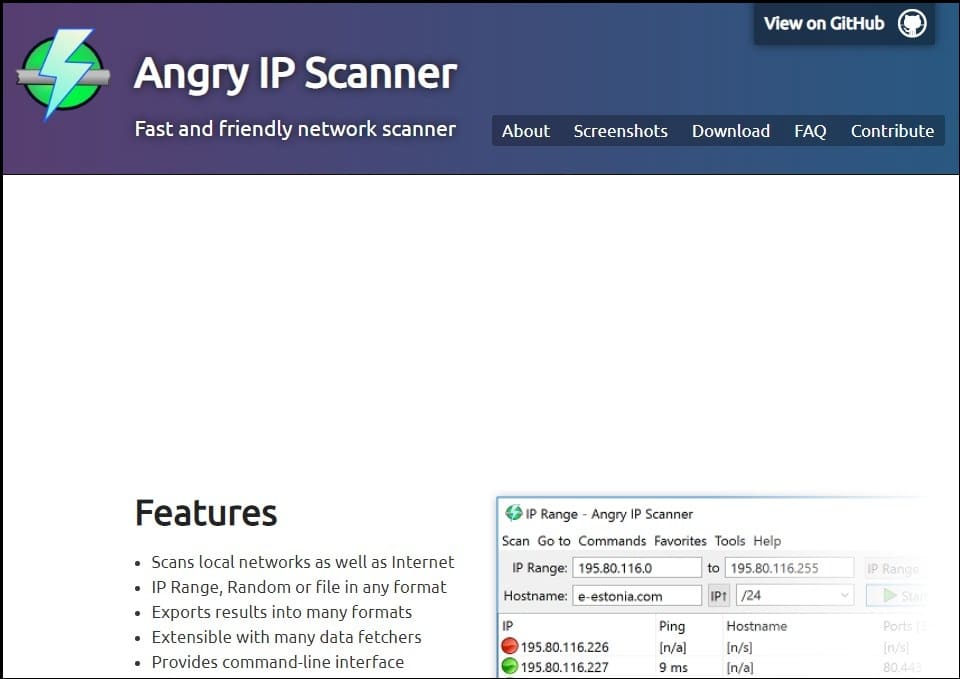
- You will see an input field to enter the IP range you want to scan. The tool also has support for scanning a full local subnet if you do not specify the IP range you want to scan.
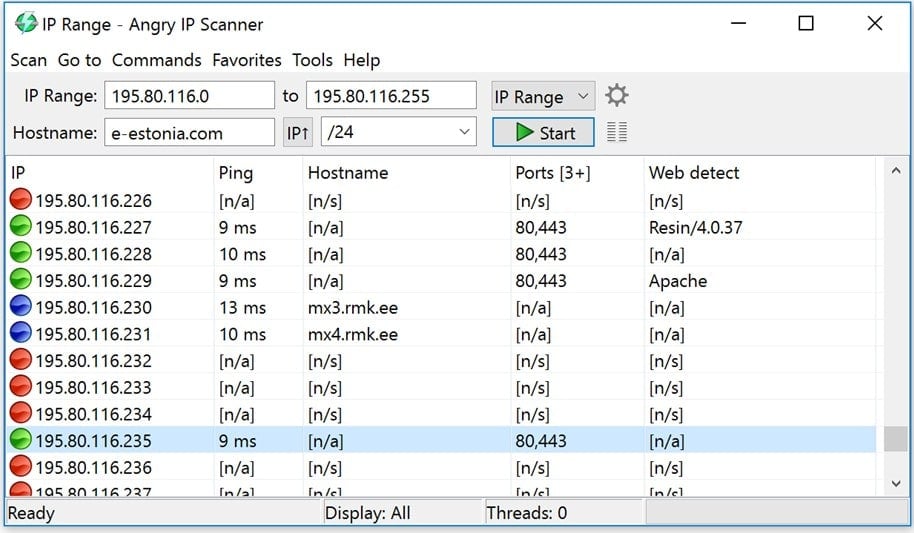
- If you have a list of IPs, you can simply upload it using the upload button instead of entering the IP range.
- Specify the hostname and click the start button. Allow the tool to finish the scanning task.
- You should see a list of scanned IP addresses, ping, hostname, and open ports
The tool is quite advanced, and the above is just a quick reference guide on how to use it. It has a lot of advanced features you can use to get the most out of your network scanning activities.
Conclusion
Network scanning is important for finding active devices and their opened ports in a network. The tool for scanning networks for data is the network scanner, otherwise known as an IP scanner.
While both IP scanners and network scanners are used interchangeably, some tools are specialized that using such a name might not be appropriate in some situations since some tools are focused more on port scanning.