How well do you know Incogniton and what it is used for? If you know little, then come in now and learn all you need to know about Incogniton, including how to integrate proxies.

It is no news that many people and businesses today have multiple accounts across different social media platforms. Unfortunately, many of these accounts have suffered blocks or bans due to policy violations.
This is because web services do not permit a user to have more than one account. If you must do that, you must do it without being detected. Unfortunately, with increasing interest in browser fingerprinting, you need more than just hiding your IP address and deleting cookies.
You also need to make protect against browser fingerprints by spoofing them. And that is where antidetect browsers like Incogniton come in. with an antidetect browser; you are able to create multiple browser profiles, each with its own browser fingerprint and environments such as cookies, cache, IP address, and history.
This article will focus more on the Incogniton antidetect browser, which is one of the new generation options available.
What is Incogniton?
When it comes to protecting the privacy of your online data, Incogniton is a good anti-detection browser that also allows you to maintain multiple browsing profiles. Each browser profile is considered a separate browser. This is because each has a unique browser environment, such as cookies, local storage, and cache.
At the point of creating a browser profile, you can configure a proxy with it, giving each a unique IP address. This gives each browser profile a unique footprint. And as such, your multiple accounts will not be detected when done correctly on Incogniton.
This antidetect software gives you control over most browser parameters used for fingerprinting. Browser profiles are saved in the cloud. However, you can decide to have them saved locally if you are not OK with saving them in the cloud.
Not saving them in the cloud will means no data synchronization across devices and team members. Yes, Incognito does have team collaboration support. It also does have support for web automation via Local API using either Selenium or Puppeteer.
Features of Incogniton

Incogniton is and will always be a stealth web browser that you can access from anywhere. Hence, as a safe way of remaining anonymous, there are a number of features that give Incogniton its uniqueness and cause it to stand out among other anti-detection browsers. In this section, we will be looking at a few of those features. Below are a few of them.
-
Bulk Profile Creation
The bulk profile creation function enables you to generate several browser profiles quickly. You can access the bulk creator by selecting “Create Bulk” from the “Browser Profile Creation” section of the left menu. The tool is highly customizable and quite advanced.
-
Data Storage

Where browser profiles are saved is one uniqueness of this service. The browser profiles are safely and securely in an online database, which makes it easy for profile sharing, team collaboration, and data synchronization. You can decide to keep your data on your own device as well. However, you are aware of the dangers associated with that.
-
Selenium Integration
Automating the processes associated with your incognito browser can help you save time. The Selenium webdriver is used by the Incogniton browser automation, however. Two ports can be set up to connect with Incogniton's Selenium integration. The general API port is the first, while the Selenium hub port is the second.
-
Paste as a Human Typing

This is a one-of-a-kind feature. As digital natives, we frequently copy and paste text into online forms when using our browser profiles. However, websites can tell based on the entry speed whether the content was typed by a person or copied and pasted. Therefore, because of this feature, you can paste text from a copied paragraph and make it appear as though it was entered by a human while using incogniton. It allows you to save time.
Best proxies for Incogniton
Proxies are not a must for you, but if you need to manage multiple accounts, create a stealth account, or hide your IP address while using Incogniton, then it becomes compulsory. Incogniton does not provide proxies – you have to do that from your end. Below are some of the best proxies to use with Incogniton.
-
Residential Proxies

Residential proxies are the best for Incogniton since the IPd they use are residential IPs, making them indistinguishable from regular users. If your task require rotating residential proxies, you have many option available to you. Providers like Bright Data, Smartproxy, and Soax are the best. For those that need static residential IPs otherwise known as ISP proxies, Netnut is the best provider so far.
-
Datacenter Proxies

If your tasks does not involve some serious automation and you target site does not ban IPs aggressively then datacenter proxies will do.
They are usually faster than residential and mobile proxies. Their only major problem is that they easily get banned. If you need datacenter private proxies to integrate with Incogniton, then Proxy-Seller and MyPrivateProxy are are the best providers for you.
-
Mobile Proxies

You will hardly need mobile proxies as residential proxies work for most difficult to access websites. However, if your target site can detect residential proxies, then you will need to make use of mobile proxies. Mobile IPs are dynamically assigned, enjoy more trust, and usually unblockable. TheSocialProxy and Hydraproxy are some of the good providers out there.
Why Do you Need Proxies for Incogniton?

Whatever the number of accounts you want to manage, Incogniton has features that let you create as many browser profiles as you need. And with this, you have no issues. However, there is one problem.
All of the browser profiles you create will still share the same IP address. And with the same IP address, the web service of target will know that they are being managed from the same computer. Proxies are the tool that will provide each browser profile a unique IP address, making them truly separate. Without proxies, Incogniton will be useless for managing multiple accounts.
While the recommendation is usually one browser profile to a proxy, you can get away with sharing one proxy for two profiles if you are using a private proxy.
For rotating proxies, you can generate as many endpoints as you want to bind each to a browser profile. Incogniton has a tool to actually test out the proxies you configure to make sure they work. This will help you avoid ip leak that will get your accounts banned.
Incogniton Proxy Integration Guide
Using Incogniton with a proxy server solution is one smallest parts of the larger management architecture. However, the proxy integration with Incogniton is very vital. Below are the few steps it takes to integrate a proxy service in the anti-detection browser successfully.
Step 1: First, visit any of your preferred proxy providers to purchase your proxies. Refer to the best proxy for Incogniton section.
Step 2: Download and install Incogniton from their website here.
Step 3: Register your account and sign in.
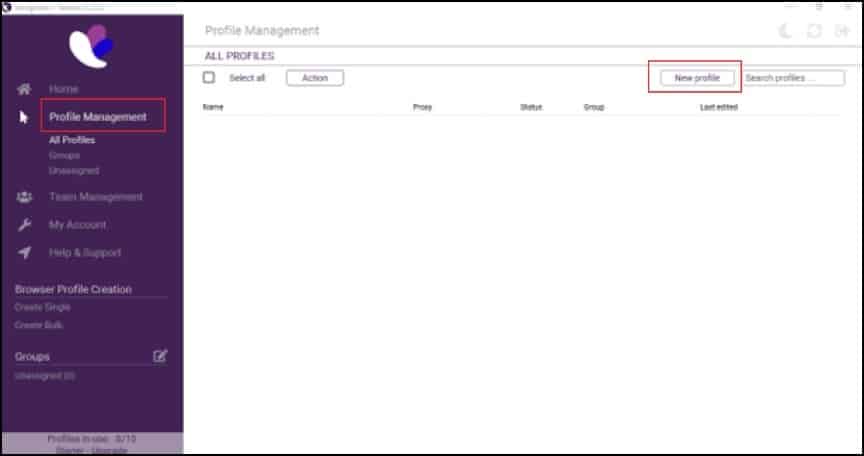
Step 4: After logging in, select “New profile” under Profile Management.
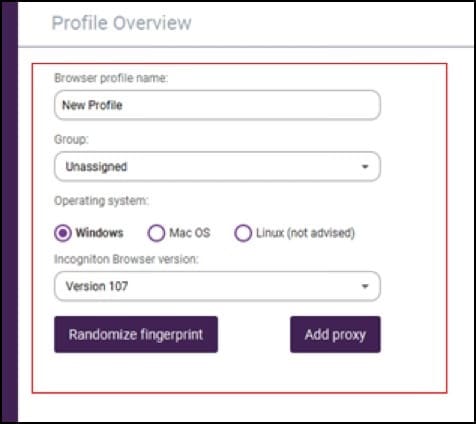
Step 5: Create the profile by entering the profile name, the group to which you wish to assign it, the version of the browser, and the OS fingerprint for your browser.
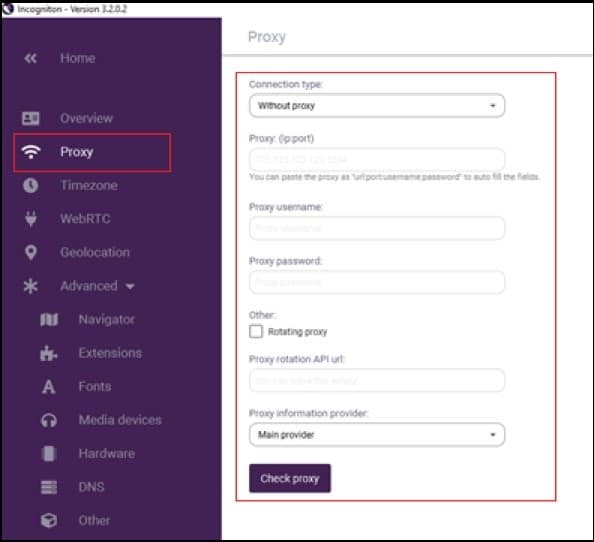
Step 6: Next is to click on Proxy in the menu on the left side. First select your connection type and fill the appropriate values for the other form fields.
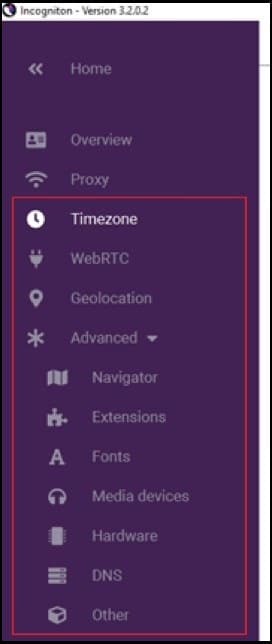
Step 7: The remaining information (time zone, location, etc.) should be filled out according to your preferences.
Step 8: Finally, on the right side of the screen, you would see a summary of all your inputs.
Step 9: Once you've finished verifying your entry, click “Create profile.”
There you have it. Your proxies and Incogniton have been integrated successfully. A browser window will open when you click “Start” on your newly created profile. You can now start using the versatility of anonymity for your web operations.
Conclusion
From the above, you should already know what Incogniton is, what it is used for, and how to integrate proxies to give it maximum protection against detection. With the right steps, you should be able to hide your browser fingerprint and avoid getting your multiple accounts blocked. We hope that this article has given you more knowledge about Incogniton and its benefits. You can look up more details about the detailed usage manual in Incogniton's knowledge base.