Close to 50 percent of smartphone users in the United States are using an iPhone. That is how popular the Apple smartphone is. iPhone is the name that comes to everyone's lips when they talk about high-end mobile devices.

iPhone and its associated devices such as the MacBook, airpod, and all of the other apple products make a great ecosystem. The premium feels and usability is second to none. And it has got great security too.
With all of its goodwill and name, you will think it is not hackable right? Well, you must be joking. Just as the device is designed to work smoothly and make our lives easier, so could the users be vulnerable and be at the mercy of online monsters.
These monsters could sometimes be hackers whose major aim is to get as much information from their target as possible. Raising kids in this new technological dispensation can be a pain in the neck, and finding a way to keep their activities safe should be a top priority.
To help you figure out seamless ways to monitor your kids and be satisfied that they are keeping it clean online, we have put together a number of spy apps to aid your spy. Spouses and employees are not left out of the spy. We shall be talking these apps soon in this article, but first, let us discuss some reasons why you may want to consider spying an iPhone.
Why Spy an iPhone?

There are many reasons why you will want to spy on someone’s iPhone. Below are some of the most popular options that are somehow legitimate depending on some factors.
-
Parental Control

Sometimes children are caught in the web of the callousness of these monsters, and they could either be pushed by Internet predators to make certain decisions that could be detrimental to either them or their parents. So, to be sure that their kids are doing the right thing on their mobile devices, some parents deem it necessary to spy on the devices of their kids.
Not only to monitor their activities on their mobile devices but also on their respective social media accounts.
-
Spy on a Spouse

With the social media dispensation, there could be chances that your spouse is cheating on you on any of them without your knowledge. Cheating results in a lot of emotional outbursts by the spouse's victim, and also questionable loyalty.
However, you need to be sure that your instinct is right by spying on their mobile device. Thankfully, there are quite a handful of spying apps that could aid your spying.
Popular Methods of iPhone Spying
In this article, we have selected the finest of spy apps that could help you monitor the activities of someone on their iPhone. Some of these apps could help you do so without having access to your target's phone. Others may need you to have one-time access for setup.
-
Using Neat Spy App
Neatspy is an online-based spying tool that helps you, spy, on the files on an iPhone device such as their photos, and videos. You can also ascertain their location by using Nestspy. You can monitor their activities on social media such as WhatsApp, Facebook, Instagram, and Snapchat, all without having physical access to their mobile device and without their knowledge. This platform is less complex and therefore is easy to use.
It could be accessed by using your desired browser, all you need is a good Internet connection. It does not even require you to jailbreak your target's iPhone as that could comprise the security configuration of their mobile device. It uses iCloud technology to get the activities of your target. This enables you to get updates on their activities on their mobile device every 5 minutes. Below is a step-by-step guide on how to use the Spy App.
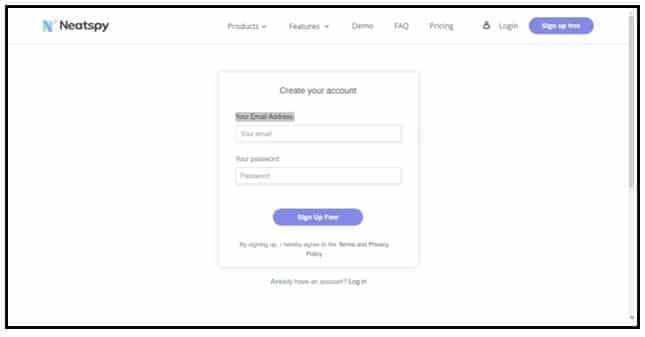
Step 1: Visit the Neatspy Sign Up page
Step 2: Enter your email and your preferred password, which is expected to be a combination of numerals and letters, and click the Sign Up button.
Step 3: The next page requires you to select the operating system of your target's device. There are two options there, Android and iOS. Select iOS.
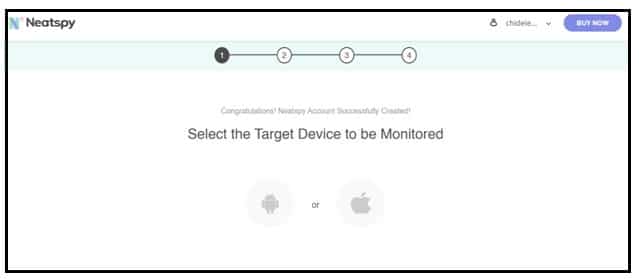
Step 4: Select your subscription plan and continue.
Step 5: The next step is to provide the iCloud details of your target.
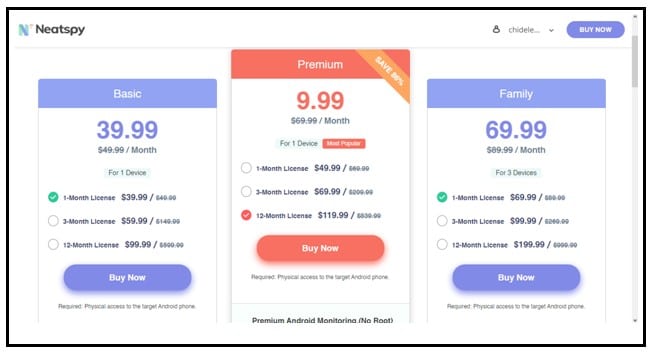
Step 6: When that is done, Neatspy will let you have access to your dashboard, which houses most features of the tool. On the dashboard, you have many options such as their call logs, messages, location, browser history, and their social media accounts.
-
Using Umobix App
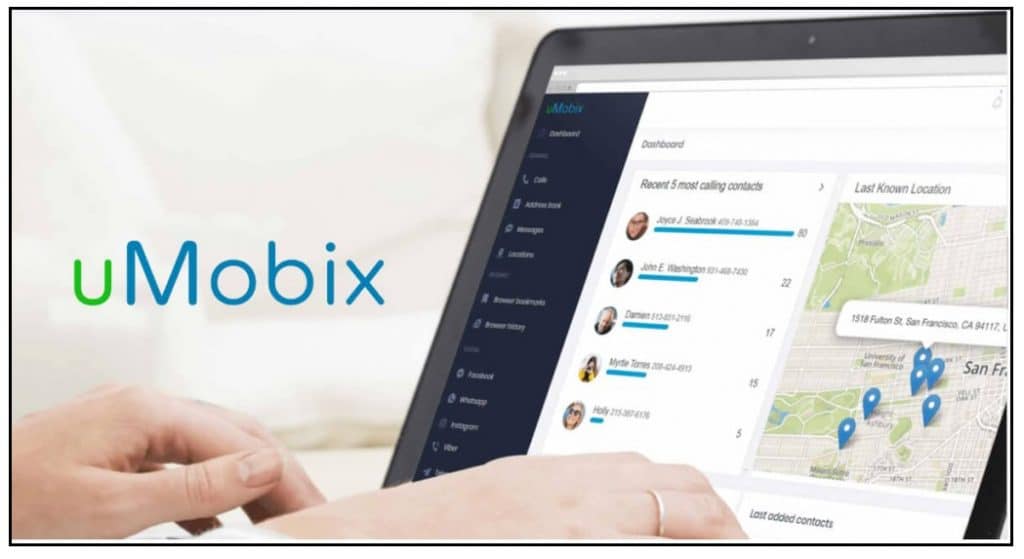
Another excellent spying app on our list is Umobix. This app is available for Android and iOS. Just like the Neatspy, the app helps you monitor the activities of your target on their mobile device without them knowing. Below are the steps to set up Umobix:
Step 1: You need to get the mobile device of your target handy in order to pass the 2FA (2-Factor Authentication) that will be sent by iPhone.
Step 2: Then you need to turn on the backup on your target's phone. To do that:
Step 3: Go to Settings on your target's device
Step 4: Tap on Apple ID
Step 5: Tap on iCloud
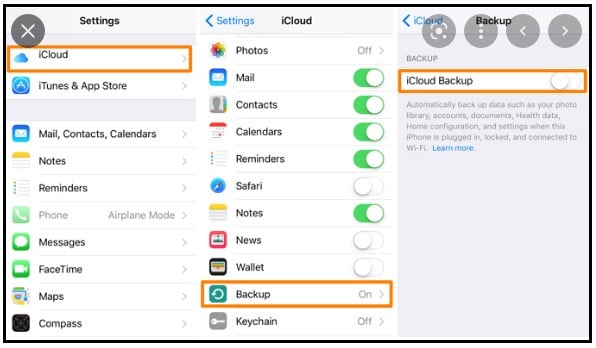
Step 6: Now you need to enable backup for every app you intend to monitor
Step 7: Tap on iCloud Back Up
Step 8: Tap on Back Up Now
Step 9: Visit their website
Step 10: On the top right of the page, click on the Try It Now button. The position of the Try It Now button depends on the device you use to visit the website. For computer devices, the button is located on the top right. For mobile phones, it is located in the middle of the screen or on the center screen.
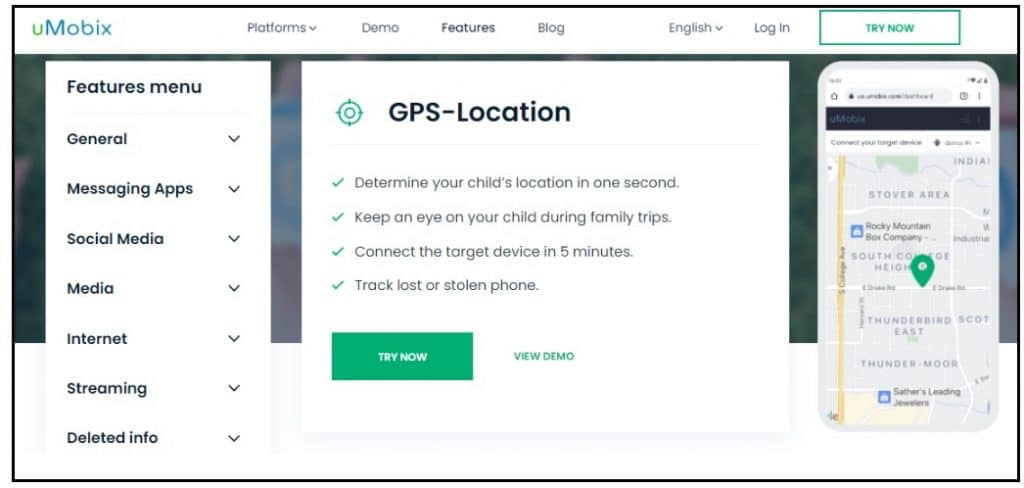
Step 11: You're required to sign up to get started. Provide your email and a password you can remember. This email will be required when you want to log in to the portal where you are going to be monitoring your target from.
Step 12: The next thing is selecting the operating system of your target. Select iOS in this case.
Step 13: Choose a subscription plan for your spy app and proceed.
Step 14: Provide the iCloud credentials of your target when promoted.
Step 15: When your account has can created, then a message will be sent to your email. The email contains a link to log in to Umobix. The email also contains your registration code. This code will be required when you are going to be installing the Umobix app on your target's device. Click the link to complete your setup
Step 16: Now it's time to install the Umobix app on your target's mobile device.
Step 17: First, you need to provide the iCloud credentials of your target's device; Apple ID, and password.
Step 18: Next step. You will receive the Apple verification code on your target's device.
Step 19: When a prompt pops on your target's device, please tap “Allow”
Step 20: Input the received code in your account and tap Enter
Step 21: That's it. The installation is over.
All you have to do now is wait for 24 hours for the app to collect information about the activities of your target and send it to the server for you to access. The features include Location, Calls, SMS, Social, and Sites, all of which reveal the activities of your target in each category.
How to Know if Your iPhone has Been Hacked
Quite a number of manifestations could signify that your iPhone has been hacked. Some of these signs could be inward or outward. Let's have a look at some of them.
-
Phone Slows Down

When your phone’s speed has changed negatively—in other words, it does not respond quickly to tasks—then there could be an app running in the background which is causing your iPhone to slow down.
-
Faster Battery and Data Drain

Of course, after some years of using your iPhone, it tends to develop battery issues but in a situation where you have not used your iPhone for a long time and its battery drains faster than normal, then there might be some apps running in the background or some activities going on behind your back, which is causing the fast drain.
In addition, when you notice that your data does not last as long as it used to, it could be a result of someone performing data-consuming activities on your phone remotely.
-
Increased Temperature

Ordinarily, your phone may heat up a bit when you are multi-tasking but does your phone feel hotter? In a kind of unprecedented way? It could be a sign that someone is using it with you remotely.
-
Strange Messages, Emails, or Calls
You go to your call logs to call someone you had called earlier but cannot find their number on your call logs. Or you meet some records of calls you did not make? These are clear indications that your iPhone is under attack.
In the same vein, when you begin to see strange email messages in your Sent Box, Inbox, or Outbox, it could mean that someone has compromised not necessarily your phone, but has once had access to your phone one time to have gotten your email login details.
How to Prevent iPhone Hack
To put your iPhone device out of the access of hackers you need to put one or two things in check. These things will not take much of your time—or are not that difficult to practice—depending on the nature of the preventive measure. Below are a few things you can do to keep your iPhone safe at all times.
Do not Jailbreak Your Phone

The Apple devices have a very good security structure, which helps keep your data well secured, but jailbreaking makes your device vulnerable to attacks. For clearance, jailbreaking is tampering with your iPhone’s security architecture, by replacing or tweaking the key components of Apple’s iOS operating system with custom applications.
This makes your iPhone begin to perform tasks that it originally would not have been able to perform without jailbreak. Undoubtedly, jailbreaking has benefits, but also be prepared for the risks.
Do not Connect to Unverified VPN:

VPNs are good to disguise your location and keep your iPhone’s IP address away from the prying eyes of hackers, however, you should be sure of the VPN you are using. Bad VPNs are designed by hackers to steal your information and direct your traffic information to store them, or even sell them. A test will help you be sure that your IP address and location other details are not revealed. You can take a quick DNS test on www.dnsleaktest.com when you have your VPN on.
Avoid Connecting to Public Wi-Fi:

Public Wi-Fi is good but sometimes might be dangerous for you. Hackers use a Man-in-the-Middle attack where a third party has access to your communication between two parties who think they are communicating directly with each other.
Some public Wi-Fi does not have adequate security and encryption that is essential for keeping phone users’ data safe. Sometimes, these Wi-Fi are set by hackers to get information of unsuspecting users. To ensure that you are on the safe side, desist from consuming public Wi-Fi indiscriminately.
Conclusion:
The above methods of spying appear similar, but each one has a slightly different setup process, you should pay attention to the details in order not to mix any of the steps up.
Unless you are spying on your kids or monitoring your spouse's activities on their phone, other reasons that are not genuine are considered criminal. Be sure you have a genuine reason to spy on someone's iPhone such as the ones highlighted above in this article, otherwise be responsible for the legal or other consequences that may ensue afterward when your victim finds out.
This article seeks to educate you on how an iPhone can be spied on and does not encourage or support spying.